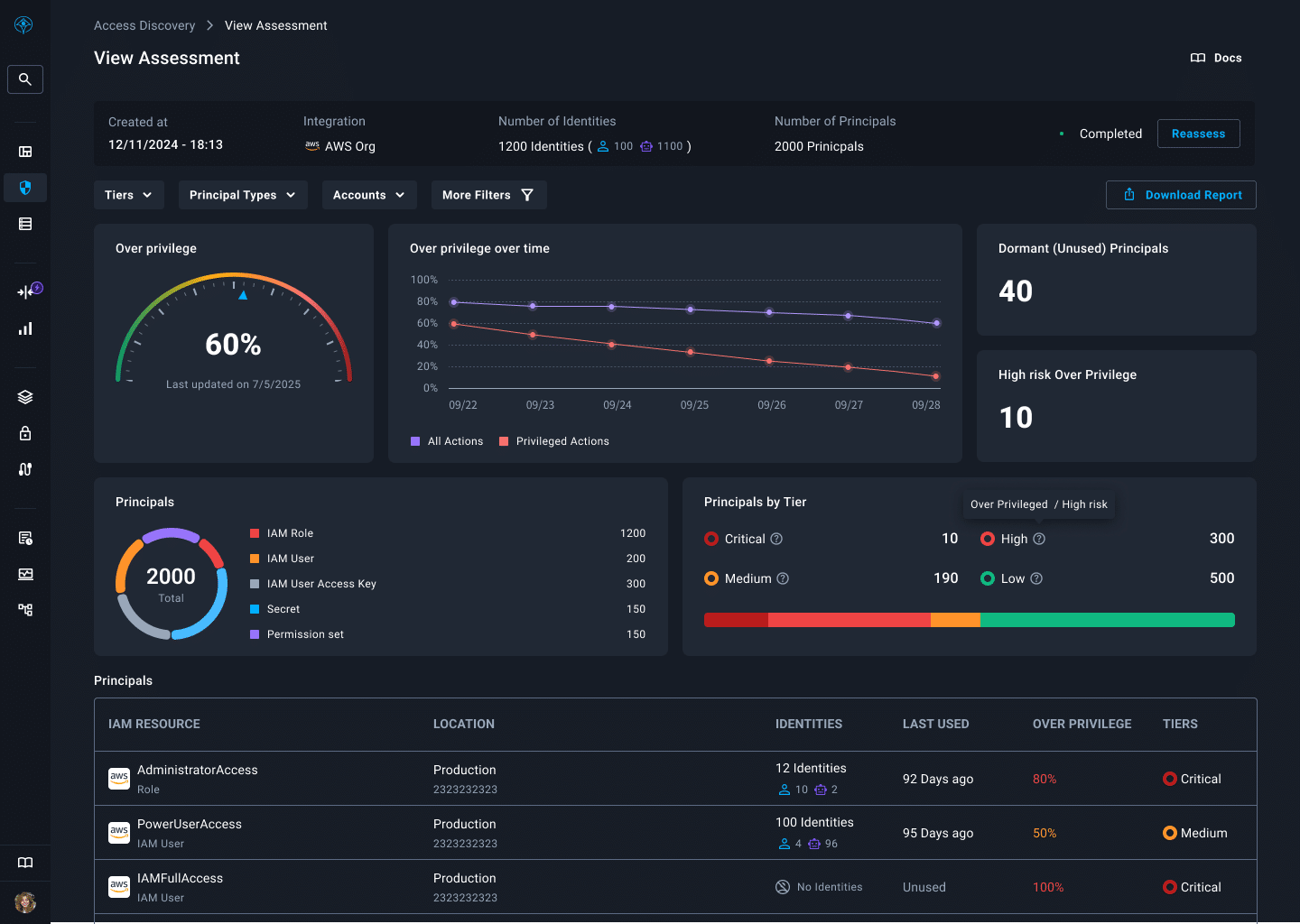
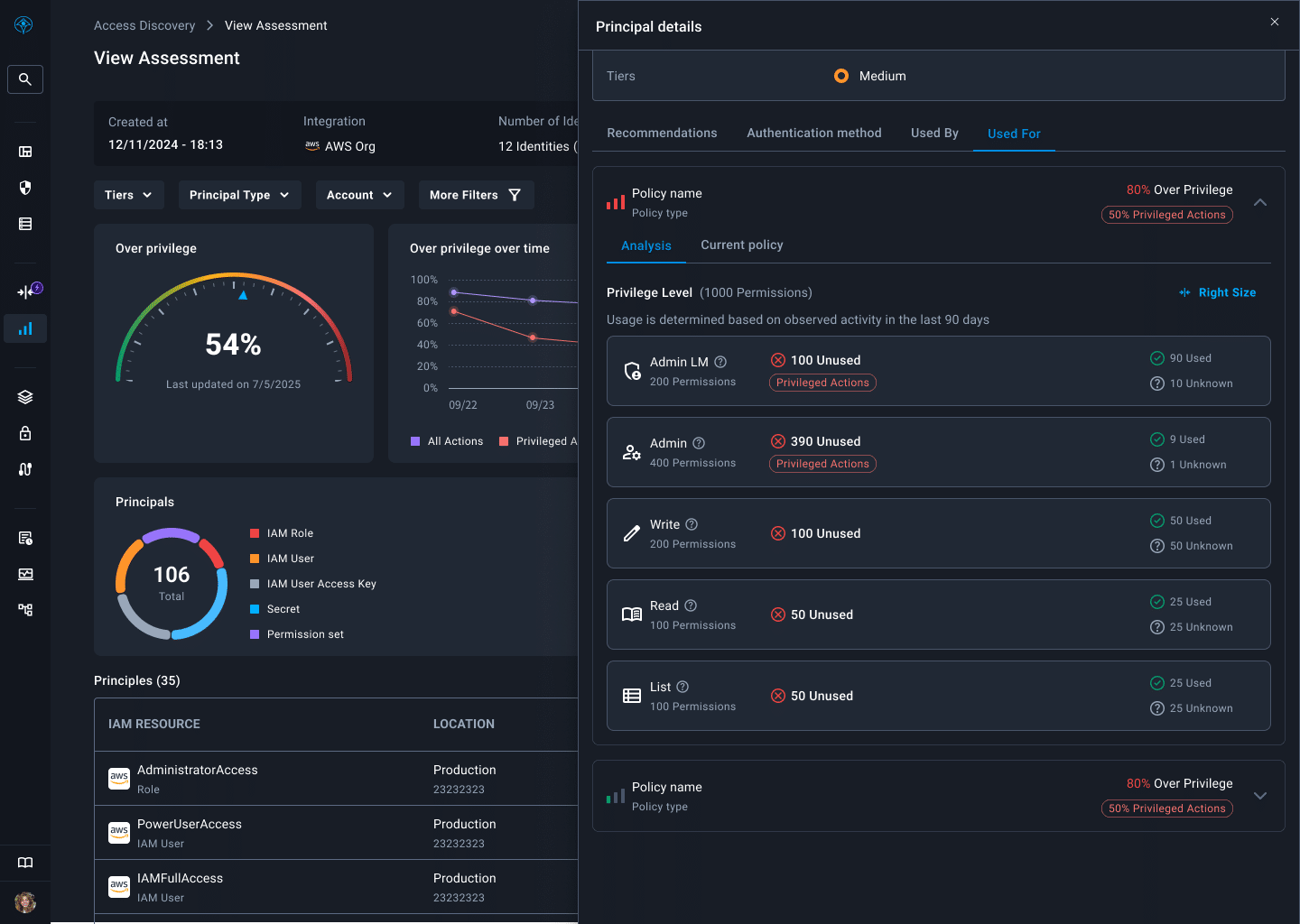
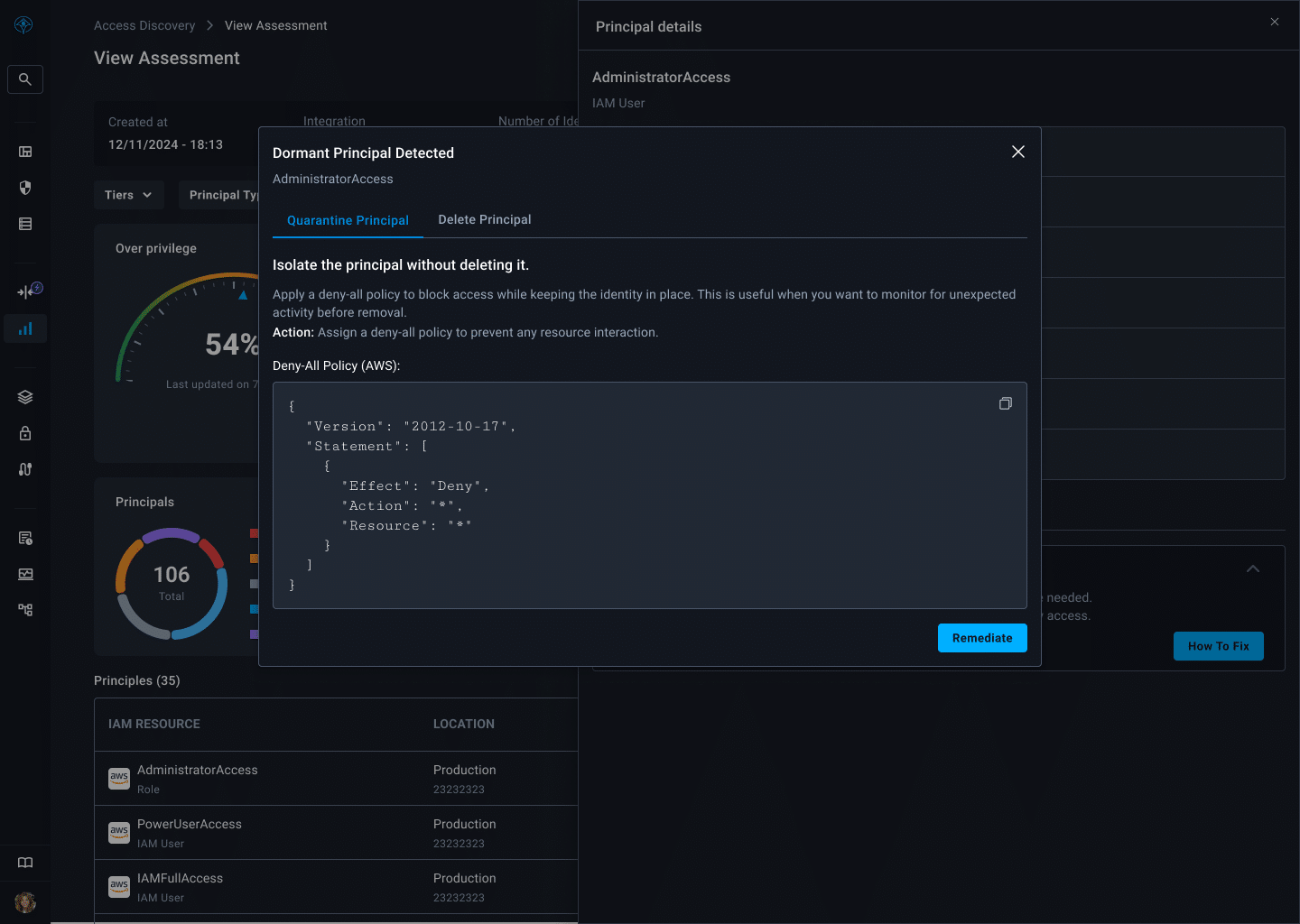
“Flexible Permission Management”
“Apono allows us to generate temporary permissions upon request on a very granular set of restrictions, delivering huge value to the business by reducing the manual provisioning phase and optimizing the day-to-day work of multiple teams, including the R&D operations and security teams. The product itself is very easy to use from both admin and user side, and it is very flexible.”