Just-in-Time Access
to Production
Use Case
Use Case
Open-ended access to critical infrastructure resources raises unnecessary risks. At the same time, too many restrictions hinder productivity and increase MTTR.
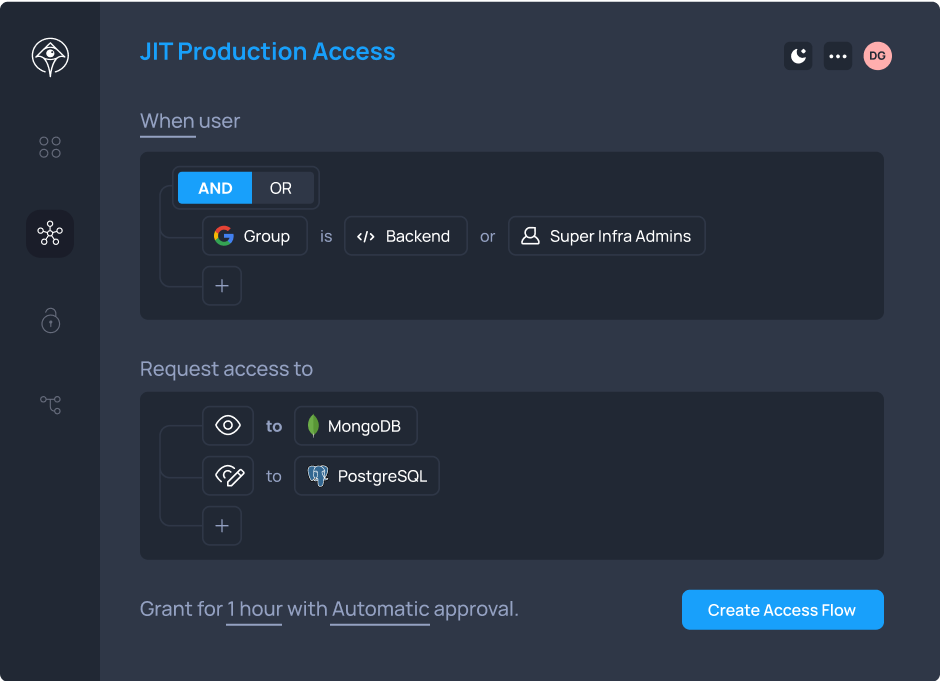
Replace standing access with time-bound access privileges to eliminate risks of account takeovers, mistakes in production or insider abuse.
Replace standing access with time-bound access privileges to eliminate risks of account takeovers, mistakes in production or insider abuse.
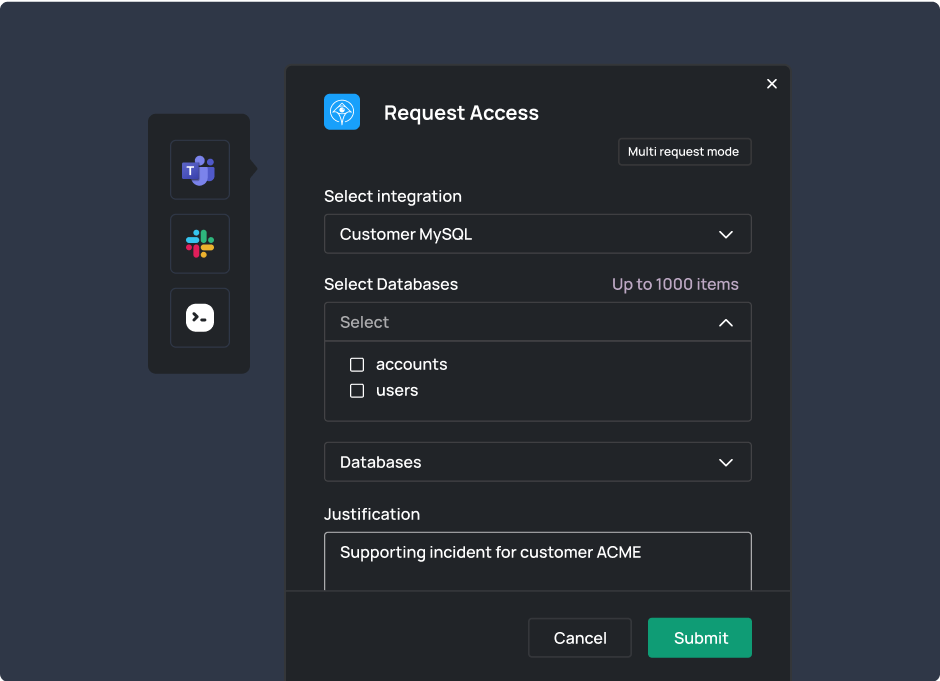
Engineers can use Slack, Teams or the Apono CLI to request access to only what they need when needed. Admins can simply define guardrails with precision via intuitive enterprise-ready workflows and bundles.
Engineers can use Slack, Teams or the Apono CLI to request access to only what they need when needed. Admins can simply define guardrails with precision via intuitive enterprise-ready workflows and bundles.
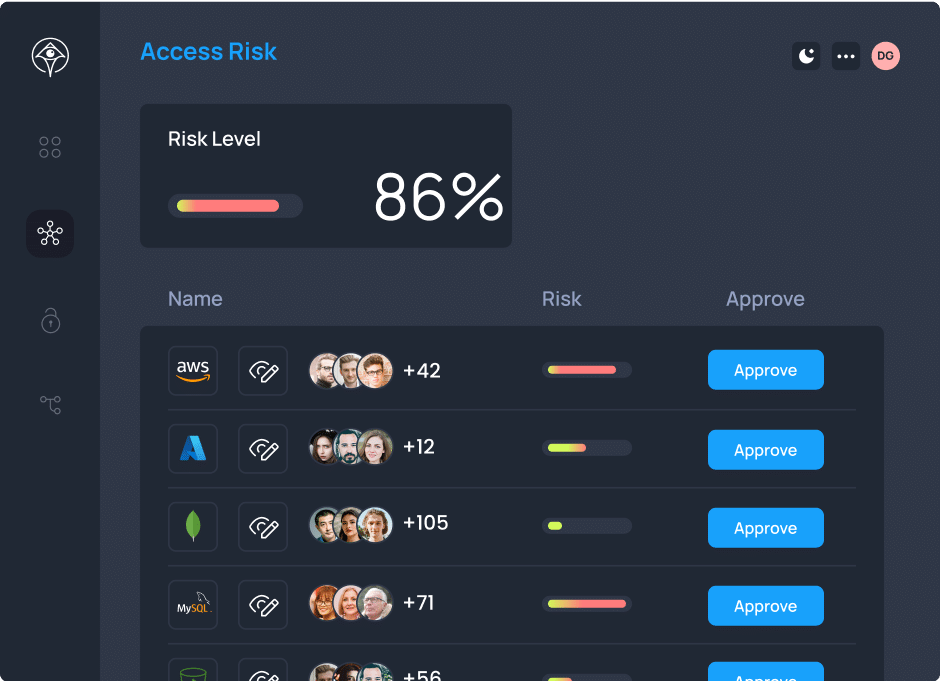
Not all users and resources require the same level of friction. Context is everything. Apono enables admins to fine tune approval flows with risk tiering controls. Automatically provision constantly utilized low risk access, enable self serve time-bound access for more sensitive resources, or ratchet up for manual approval to protect your crown jewels.
Not all users and resources require the same level of friction. Context is everything. Apono enables admins to fine tune approval flows with risk tiering controls. Automatically provision constantly utilized low risk access, enable self serve time-bound access for more sensitive resources, or ratchet up for manual approval to protect your crown jewels.
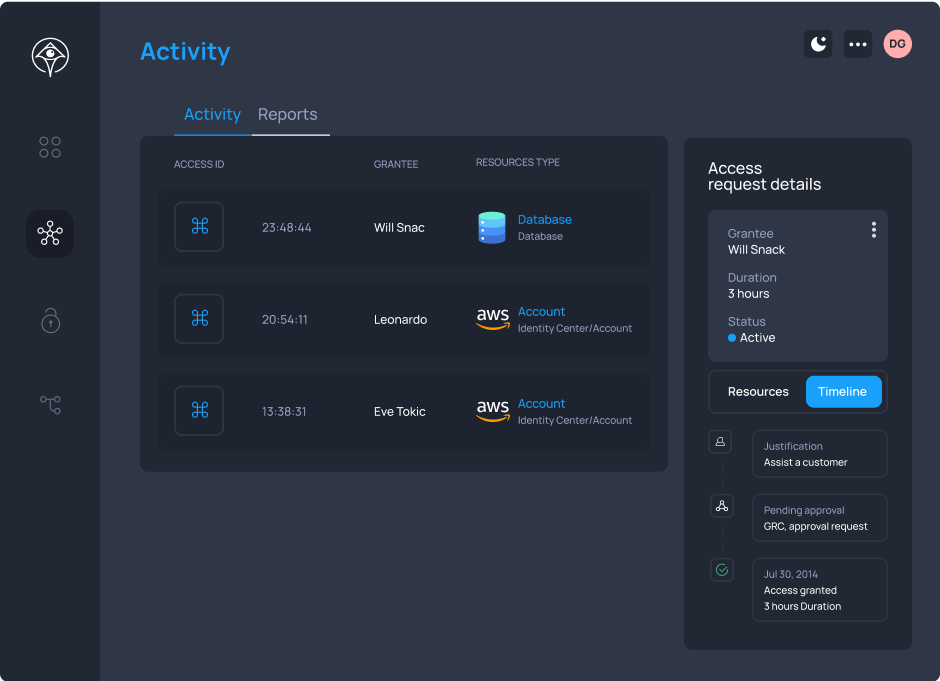
Continuous auditing of every action ensures secure use and accountability. Apono provides detailed reporting for easy investigation and anomalous access detection, alerting and response.
Continuous auditing of every action ensures secure use and accountability. Apono provides detailed reporting for easy investigation and anomalous access detection, alerting and response.
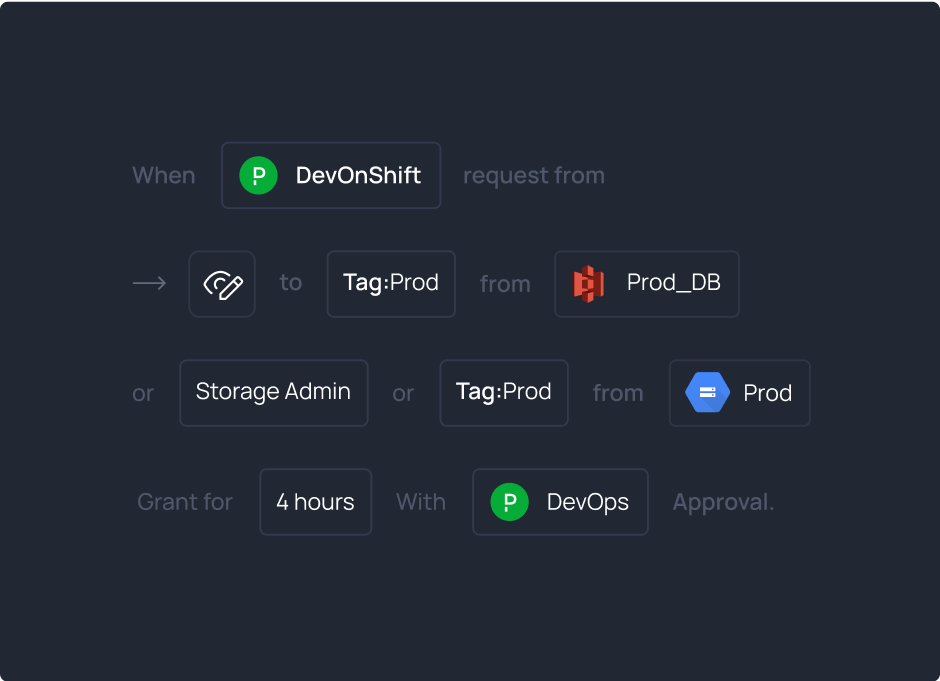
Improve MTTR by empowering incident responders to to receive the access they need immediately. Dynamically scope access privileges to the task at hand, using the context from OnCall Shift Systems and ITSM tools to provision Just-In-Time access automatically.
Improve MTTR by empowering incident responders to to receive the access they need immediately. Dynamically scope access privileges to the task at hand, using the context from OnCall Shift Systems and ITSM tools to provision Just-In-Time access automatically.
“Apono generates temporary premissions upon request based on a very granular set of rules. Delivering huge value by reducing the attack surface while optimizing efficiency.”

Information Security Manager