Create a workflow
Eliminate Standing Privileges with Secure, Right-Sized AWS Access
Enable Just-in-Time and Just-Enough-Access across your AWS environment

Amazon Web Services (AWS) is a cloud computing platform provided by Amazon. It offers a wide range of services and products that can be used to build and manage applications and infrastructure in the cloud. AWS provides a secure and scalable environment for businesses to run their applications, store their data, and access a wide range of computing resources on demand.
Integration Overview:
Apono helps organizations achieve Zero Standing Privileges (ZSP) by eliminating permanent privileged access to systems, cloud environments, databases, and other critical resources.
Apono connects to your individual AWS Accounts or entire AWS Organizations, continuously discovering your environment—from core services like S3, EC2, EKS, Redshift, and Lambda to supporting components such as databases and IAM resources (roles, users, groups, and policies). This empowers security teams to enforce fine-grained, dynamic, and context-aware access policies.
Through Just-in-Time (JIT) and Just-Enough-Access (JEA) provisioning, access to AWS resources is granted only when required and automatically revoked—reducing over-privileged accounts, minimizing the attack surface, and maintaining operational agility without compromising security.
Use Cases
JIT and Just Enough Access
- Provision real-time access to AWS environment.
- Ensure right-sized permissions and enforce strict controls on access provisioning.
- Minimize unauthorized access risk and reduce the blast radius of security breaches.
Secure Break-glass Access
- Grant just-in-time, task-specific access to on-call engineers during incidents.
- Scope and revoke access automatically based on context from OnCall and ITSM tools.
- Ensure fast, secure incident response while enforcing least-privilege access with Apono.
Risk and Compliance
- Achieve Zero Standing Privilege by reducing over-privileged and unused permissions by over 96%.
- Simplify audits with Apono’s detailed reporting, anomaly detection, and comprehensive access activity logging.
Integrate with Apono
in 3 easy steps
Just three simple steps are all it takes to enable Just-In-Time access with Just Enough permissions to your cloud assets and resources.
Connect Apono to AWS
Gain instant visibility into all AWS resources—continuously discovering new ones as they are deployed.
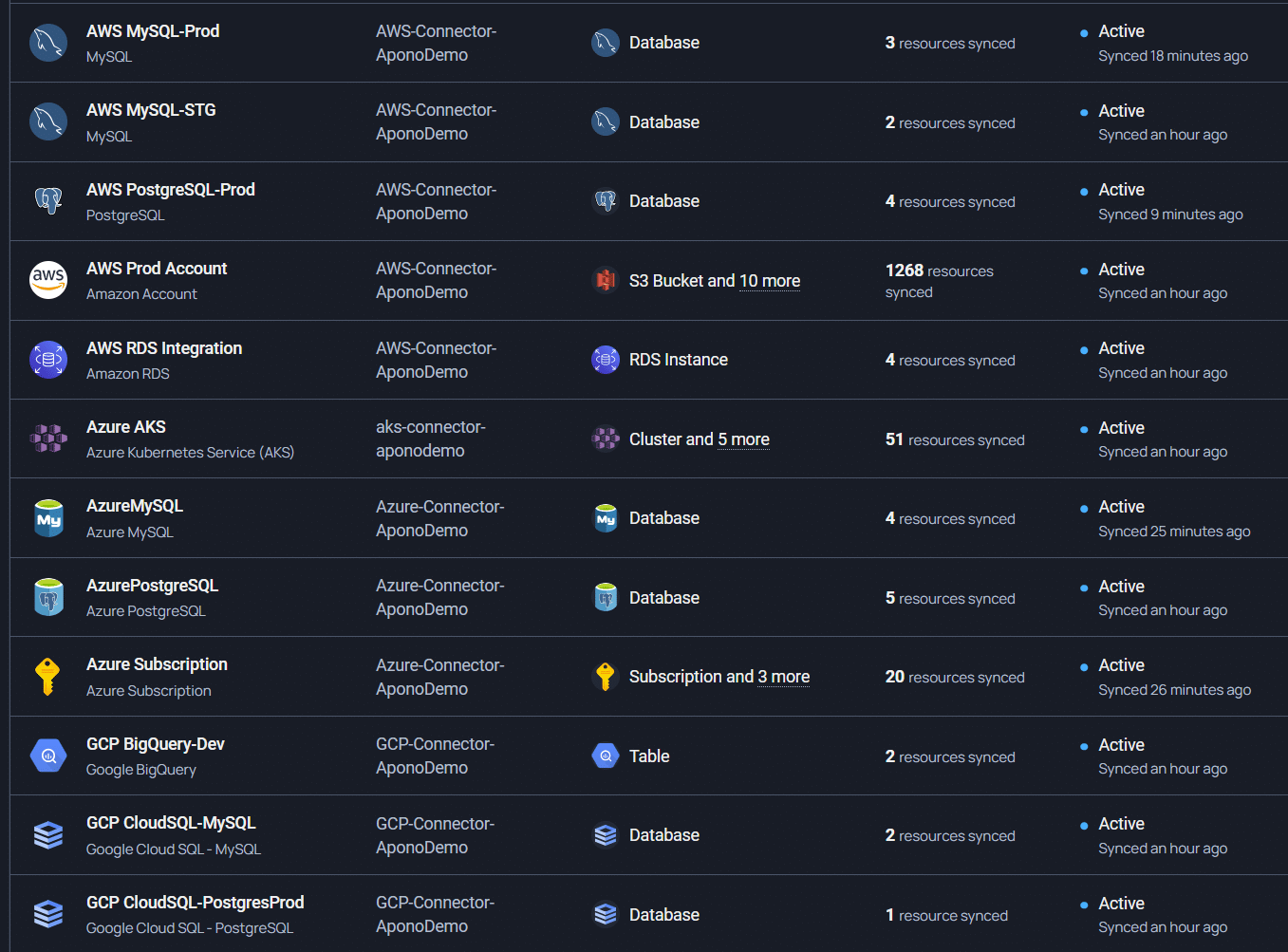
Discover why companies—from mid-sized enterprises to Fortune 500s—trust Apono for streamlined access management.
Gain full access and visibility for both human and NHI
Automate and centralize access
Leverage over 100 integrations


