Cloud-Native Access Governance
Privileged Access Challenges in the Cloud
Constantly expanding attack surface
Requires
continuous discovery.
Fast TTM and agile development
Requires
dynamic
access policies.
Every user is a privileged identity
Requires
replacing admin
with Just Enough.
Managing Privileged
Access Risk in the Cloud
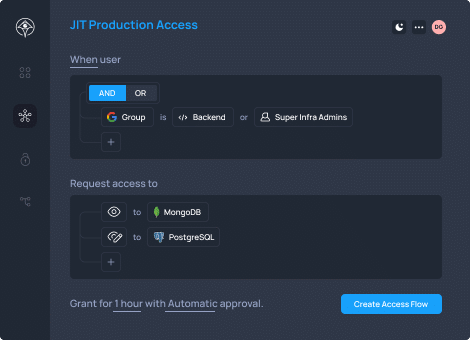
Eliminate Standing Privileges with Just-in-Time Access
Eliminate Standing Privileges with Just-in-Time Access
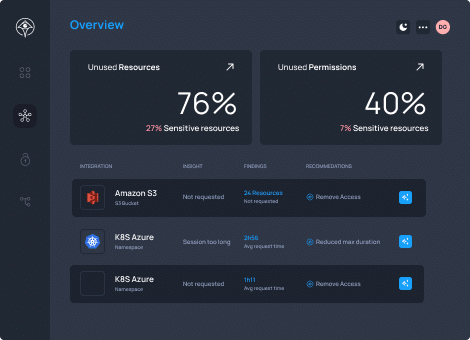
Reduce the Blast Radius with Just-Enough Privileges
Reduce the Blast Radius with Just-Enough Privileges
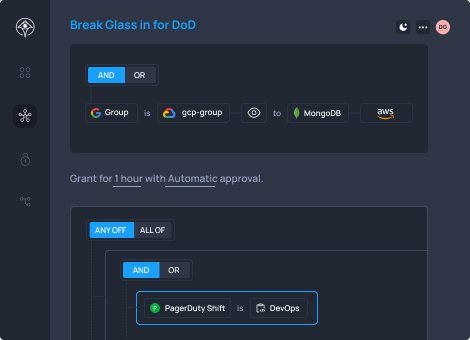
Empower Faster Response with Efficient Privilege Elevation Delegation
Empower Faster Response with Efficient Privilege Elevation Delegation
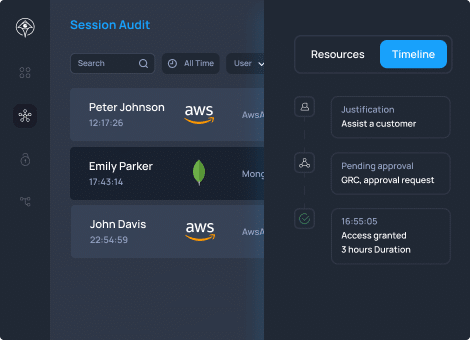
Audit All Access Activities
Audit All Access Activities
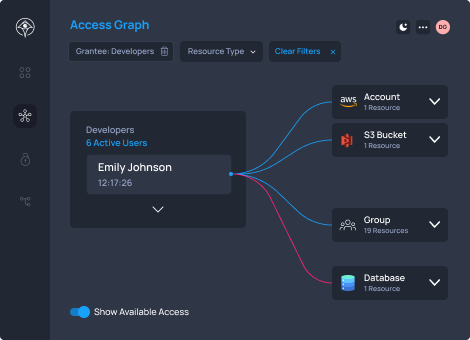
Detect and Respond to Access Threats
Detect and Respond to Access Threats
“Faster access, saved time, prevented breaches.”
“
“We’ve reduced the amount of time it takes people to get access to the things they need to do their job. We freed up the team’s time. And on top of that, we’re preventing tens of millions of dollars of potential data breach”.
Director of Cloud Infrastructure

