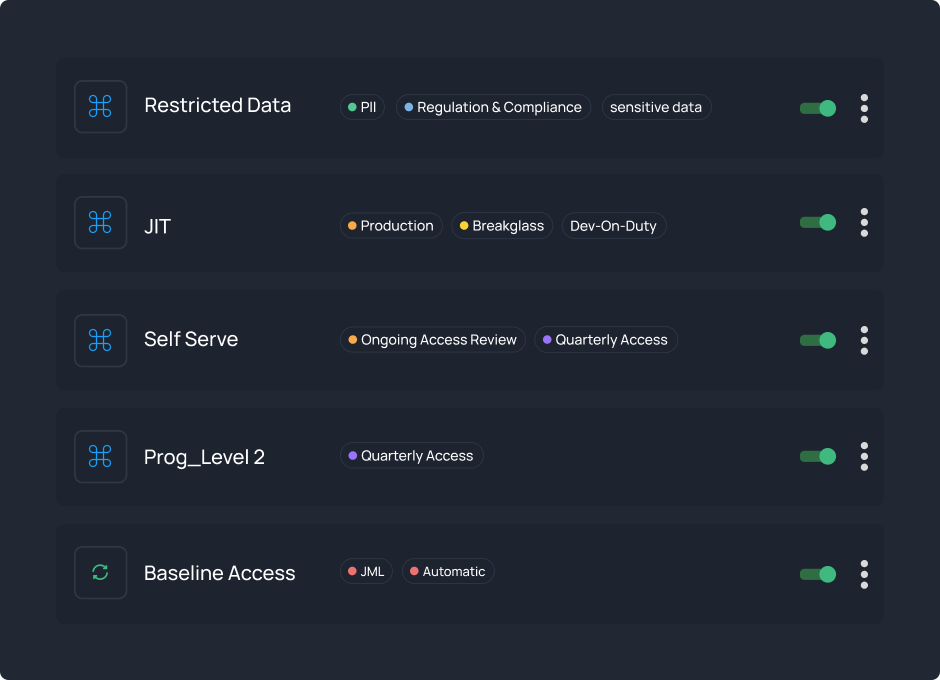
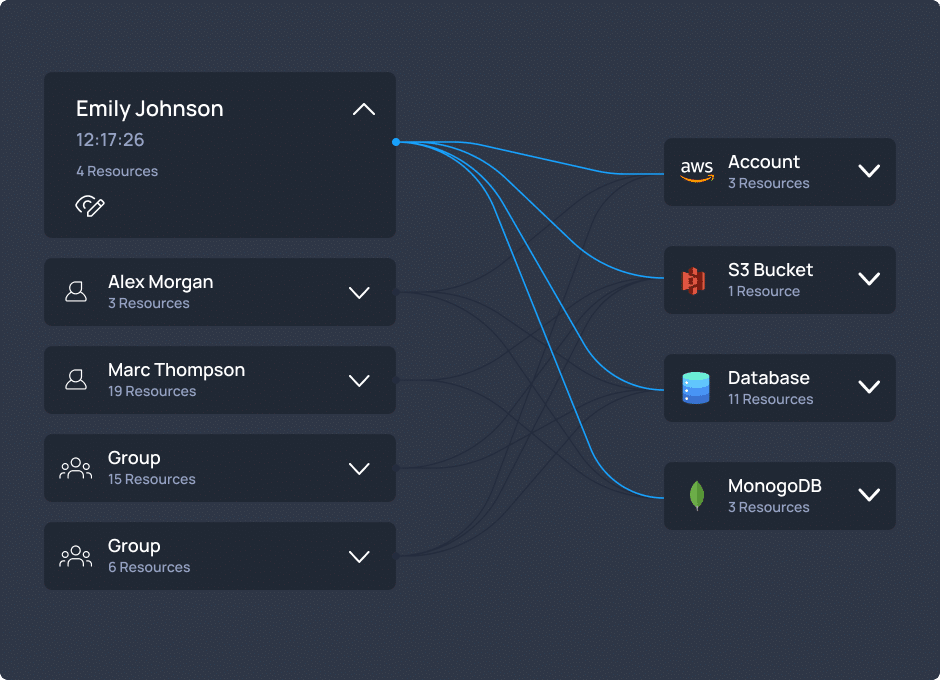
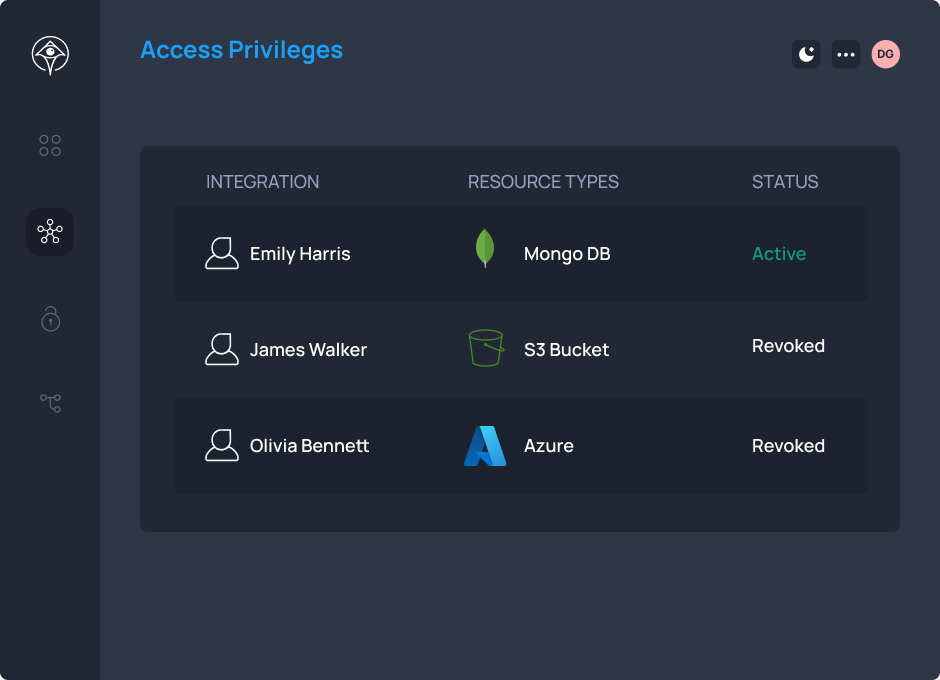
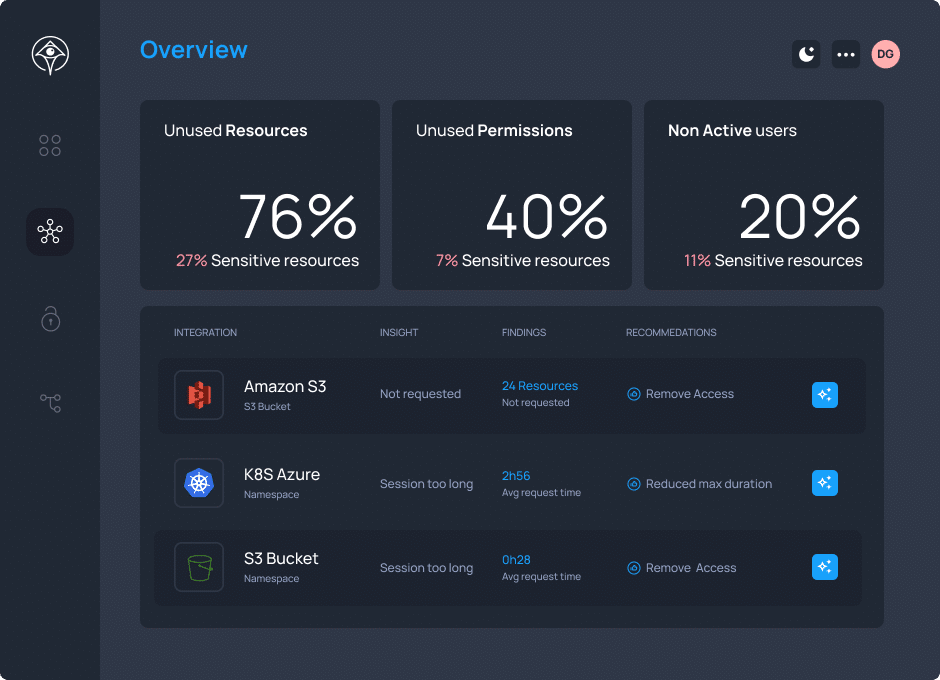
“Faster access, saved time, prevented breaches.”
“We’ve reduced the time it takes people to get access to the things they need to do their job. We freed up the team’s time. And on top of that, we’re preventing tens of millions of dollars of potential data breach”.