Quick Learn: The Three Most Common Complaints in Access Management

The Apono Team
December 2, 2024

We recently started a new blog series featuring our CEO and co-founder Rom Carmel. In this series, we discuss real issues from the field. So, check out what Rom Carmel has to say about the three complaints he hears the most in access management.
“I speak to CISOs and security leaders all the time. There’s a lot they want to fix about the way identity works today, especially in their cloud environments. The three most common complaints I hear are listed below.”
1. Too much access risk.
Organizations are juggling a growing array of systems, tools, and data. While these resources are essential for productivity and innovation, they also come with significant risks. One of the most overlooked yet critical risks is excessive standing privileges—permissions that employees or systems retain long after they’re needed.
This issue isn’t just about tidiness in managing permissions; it’s about security, resilience, and minimizing potential damage during an incident. Every person with access they don’t need right now is a liability, creating unnecessary risk and potentially catastrophic consequences.
The Danger of Standing Privileges
Standing privileges are like leaving all the doors in a house unlocked because someone might need to use one in the future. While convenient, it dramatically increases the potential for a break-in.
Here’s how excessive privileges create compounding risks:
- Expanding the Blast Radius
In cybersecurity, the blast radius refers to the extent of damage an incident can cause. When too many people have unnecessary access, the blast radius of a breach grows exponentially. A compromised account with access to sensitive systems becomes a gateway for attackers, allowing them to move laterally across the network, exfiltrate data, or cause widespread disruption. - Human Error Magnified
Employees with unnecessary privileges might unintentionally misuse them, delete critical data, or make configuration changes that create vulnerabilities. The more permissions granted, the greater the chance of accidental missteps. - Attackers’ Dream Opportunity
Excessive privileges are a goldmine for bad actors. Phishing attacks and credential theft are more effective when attackers know that any compromised account could yield the keys to sensitive systems. Standing privileges eliminate friction for attackers, offering them a direct route to the heart of your operations.
Why “Just in Case” Is Dangerous
Granting broad access “just in case” or failing to revoke permissions when they’re no longer needed is common. It’s often rooted in a combination of trust and convenience:
- Trust: “We know our team won’t misuse their access.”
- Convenience: “It’s easier than managing access dynamically.”
However, these rationalizations ignore the reality of modern security threats. Trust is not a control, and convenience is no defense against attackers who thrive on exploiting lapses in access management.
Principles for Managing Access Risks
Organizations need to shift to a least privilege model, granting users and systems only the permissions necessary to perform their current tasks. When access is no longer needed, it should be revoked immediately. Here’s how to approach this transformation:
- Implement Just-In-Time (JIT) Access
JIT access ensures that permissions are granted only when they’re actively required. For example, a developer needing to deploy code might gain temporary admin privileges for the duration of the task. Once the task is complete, access is automatically revoked. - Audit and Monitor Continuously
Regular audits can identify users with unnecessary access. Automated monitoring tools can flag unusual activity or permission creep, ensuring risks are caught early. - Adopt Zero Trust Principles
In a zero-trust framework, no user or system is trusted by default, regardless of their position or historical behavior. Access requests are verified in real-time, with strict controls on who can do what. - Educate Your Teams
Often, employees don’t realize the risks associated with unnecessary privileges. Training on secure access practices can build awareness and foster a culture where security is a shared responsibility.
The Bottom Line
Standing privileges are a ticking time bomb, unnecessarily inflating the potential impact of security incidents. By adopting a least privilege approach, implementing dynamic access controls, and fostering vigilance, organizations can dramatically reduce their exposure to risk.
In a world where cyberattacks are inevitable, the size of the blast radius is something you can—and must—control. Every unnecessary access point closed is another step toward a more resilient, secure future.
Don’t wait for an incident to expose the gaps in your access management strategy. Act now to shrink the blast radius and protect your organization.
2. Reducing User Permissions.
Reducing user permissions is one of the most challenging tasks in access management. Engineers and other privileged users often resist the idea, fearing it will slow them down or hinder their ability to work effectively. And let’s be honest—they’re not entirely wrong.
Permissions often feel like tools of efficiency: the more you have, the less you need to wait for approvals or navigate access bottlenecks. But what’s often overlooked is the hidden cost of excessive permissions: increased security risks and operational chaos during incidents.
The good news? It’s possible to balance security and productivity if we approach the issue with the right mindset.
Why Permissions Need to Be Tightened
Excessive permissions are a liability. Each unnecessary access point expands the potential damage of a breach. Attackers and malware don’t care if permissions are unused; they exploit them the moment they’re available. Reducing permissions isn’t about making life harder—it’s about protecting systems and people.
How to Reduce Permissions Without Alienating Users
1. Collaborate, Don’t Dictate
Start by involving the users affected. Engineers, developers, and admins know their workflows best. Work with them to understand their needs and identify areas where permissions are genuinely required versus where they’ve become “nice to have.”
2. Introduce Temporary Access Solutions
Adopt Just-In-Time (JIT) access models that grant permissions for specific tasks or timeframes. This way, users can still get the access they need without holding on to it indefinitely.
3. Communicate the Why
Explain the risks of standing permissions clearly. Users are more likely to accept changes when they understand the stakes—both for the organization and for their own work.
4. Showcase Improved Efficiency
Demonstrate how well-implemented access controls can streamline operations. For example, automated request systems or pre-approved workflows can reduce the time spent chasing approvals.
Reducing user permissions is never going to be entirely painless, but it doesn’t have to be disruptive. By involving users in the process, implementing temporary solutions, and focusing on clear communication, organizations can create a secure environment without sacrificing productivity.
After all, the goal isn’t to limit capability—it’s to ensure that the right people have the right access at the right time.
3. No Centralized Location for Managing Access.
Managing access in today’s tech landscape often feels like a scavenger hunt. You’re working in your Identity Provider (IDP), navigating multiple cloud environments, diving into databases, configuring servers, and manually tweaking policies across your infrastructure. Each step adds complexity, making it difficult to enforce secure policies and turning access audits into a logistical nightmare.
This fragmented approach doesn’t just slow you down—it also increases risk. When there’s no centralized way to manage access, it’s easy for permissions to slip through the cracks, leading to over-privileged accounts and potential vulnerabilities.
Centralized access management isn’t just about convenience—it’s about creating a safer, more efficient environment for your teams. With Apono, you can reduce friction, enforce least privilege, and maintain security without the headaches of juggling countless tools.
It’s time to simplify access and focus on what really matters.
Apono: Centralizing Access for Security and Simplicity
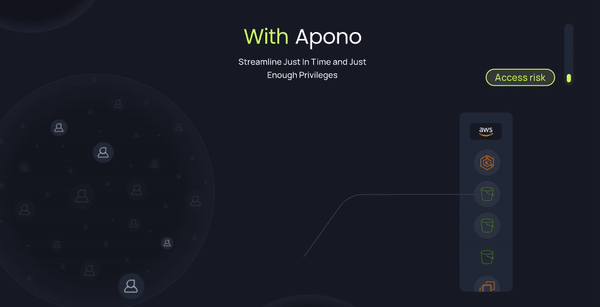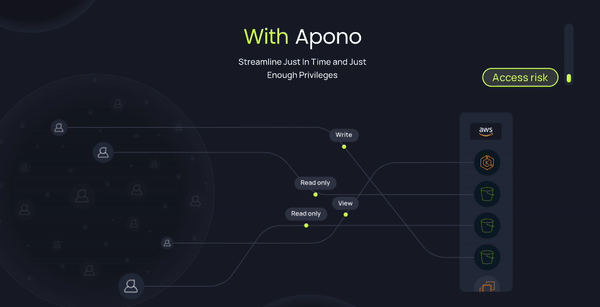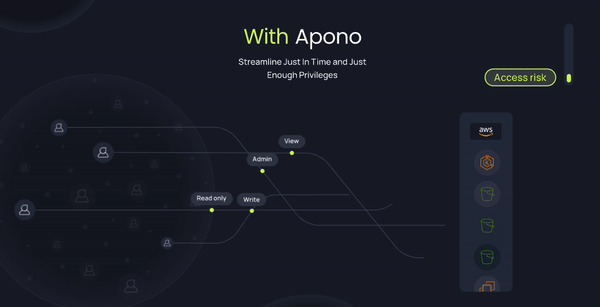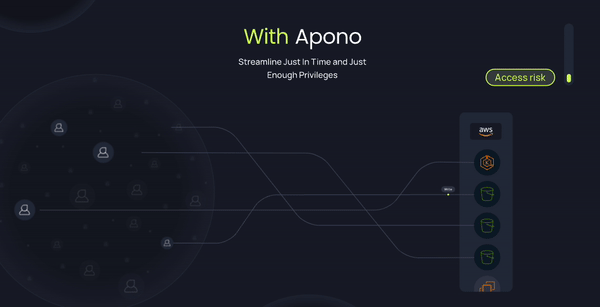
We built Apono to solve these exact challenges. With Apono, your team can:
- Manage All Access in One Place: No more hopping between systems—Apono provides a unified platform for managing access to all your modern resources and environments.
- Enable Least Privilege: Grant users the exact access they need, exactly when they need it, without unnecessary standing privileges.
- Streamline Just-In-Time (JIT) Access: Allow temporary access for specific tasks, ensuring permissions expire when they’re no longer required.
- Simplify Auditing: With everything centralized, access audits become fast, transparent, and straightforward.





