Temporary Access To Cloud SQL

Ofir Stein
January 24, 2023

Table of Contents
CloudSQL Access Controls
Securing the development environment is a critical challenge for DevSecOps teams that must navigate multiple cloud environments and technologies. To improve collaboration between developers, security professionals, and IT operations staff, we need to provide secure access to physical networks and services—which often include providing elevated levels of permissions for databases such as CloudSQL. Ultimately, you should come away with an understanding of how to securely grant developers increased privileges in their public cloud Cloud SQL environments without sacrificing any security posture or control.
Managing Permissions in CloudSQL
This blog post will explore how to efficiently manage secured elevated permissions to Cloud SQL, an enterprise database service offered on Google Cloud Platform. With Apono strategies, you can make sure that only those who need it have access to the right information while minimizing both project overhead and organizational risk. Let’s dive in!
Using Apono To Provide Temporary Access to CloudSQL
Your first step in create an Apono account, you can start your journey here.
Follow the steps at our CloudSQL Integration Guide.
Now that Apono is set you can start creating Dynamic Access Flows:
- Automatic Approval Access Flows – Using admin defined context and pre defined role to provide automatic access to CloudSQL resources.
- Manual Approval Access Flows – Using admin defined context and pre defined role to provide automatic access to CloudSQL resources.
Using Apono declarative access flow creator you will be able to simply define:
- Approvers
- User Group (round-robin)
- Single User
- Automatic – Contextual
- Requesters
- User Group
- Single User
- Resource
- Single Resource
- Pre-Defined Resource Group
- Partition of a resource
- Duration
- By Hours
- By Days
- Infinite
Example: Cloud SQL Automatic Approval Access Flow:
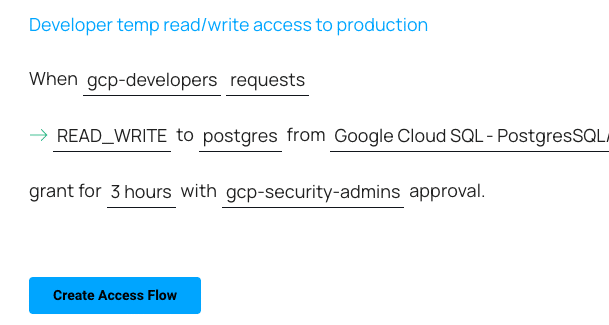
Example: Cloud SQL Manual Approval Workflow:
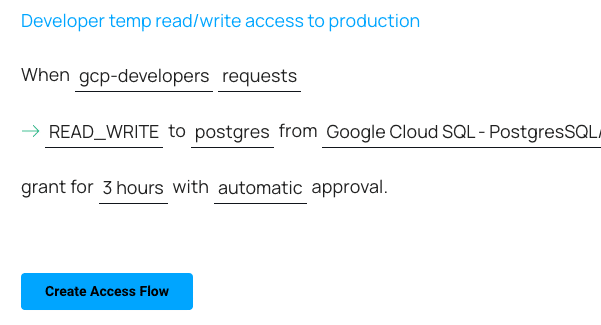
Temporary access to Cloud SQL allows you to specify a predetermined period during which certain IP addresses or IP ranges are permitted to connect to the database. Once the defined duration expires, access to the instance is automatically revoked.
The temporary access feature is particularly beneficial when you require short-term access for specific purposes, such as granting temporary database privileges to third parties or clients. By employing temporary access, you can avoid the need to permanently add unfamiliar IP addresses to the instance’s authorized network list, bolstering the overall security of your Cloud SQL deployment.
The duration of temporary access can be customized to meet your requirements, ensuring that connectivity is available for an extended period. This flexibility allows you to accommodate projects or collaborations that demand longer-term access to your Cloud SQL instance. Once the designated period concludes, the system will automatically remove the authorized access, safeguarding your database from unauthorized connections.
Streamlined Access. Frictionless Security.
With Apono, companies satisfy customer security requirements and dramatically reduce attack surfaces and human errors that threaten commerce. Apono liberates DevOps teams to deliver more for customers and the businesses without delay.




