Mastering the Art of Least Privilege Access Implementation: A Comprehensive Guide

Rom Carmel
June 4, 2024
The concept of least privilege access has emerged as a paramount principle, serving as a cornerstone for robust identity governance and access management strategies. By adhering to this tenet, organizations can effectively mitigate the risks associated with account compromises, insider threats, and unauthorized access to sensitive resources. However, achieving least privilege access across intricate, sprawling identity environments is no simple feat, often presenting substantial challenges that demand meticulous planning and execution.
Understanding the Principle of Least Privilege Access
The principle of least privilege access, a fundamental element of zero trust security, is predicated on the notion of granting individuals access solely when they require it to fulfill their job responsibilities and for no longer than necessary. By enforcing this principle, organizations can significantly reduce the likelihood of account compromises and minimize the potential impact of a compromised account or insider threat.
Why is it Important?
According to a recent report from the Identity Defined Security Alliance (IDSA), 22% of businesses see managing and securing digital identities as the number one priority of their security program, up from 17% in 2023. More than half of respondents (51%) said they now see it as a top three priority, and another 18% see security digital identity as a top five priority. Only 2% of businesses don’t see securing identities as a top 10 priority. This trend of increasing priority is a positive sign of the recognition of the importance of identity.
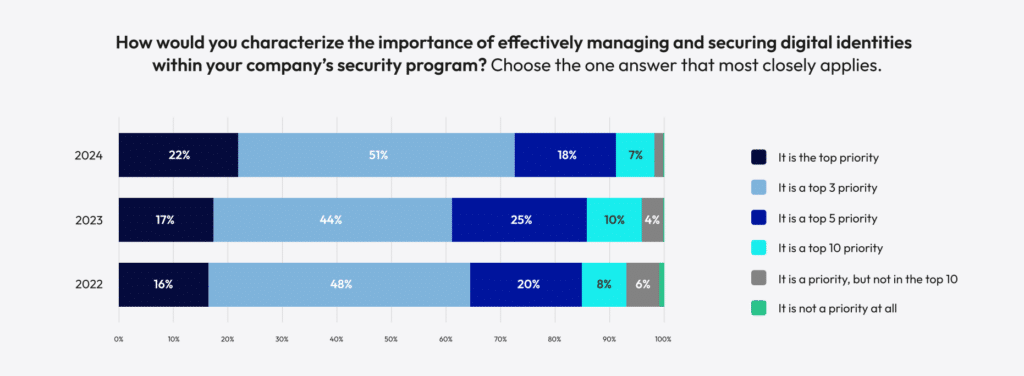
“Identity-related incidents are on the rise, emphasizing the need for strong identity security measures,” IDSA executive director Jeff Reich said in a news release. “Many of today’s major breaches result from sophisticated phishing and social engineering attacks or not having multi-factor authentication. These incidents not only impact operations, they cost a fortune—UnitedHealth experienced a $872 million loss from the Change Healthcare cyberattack,” Reich continued. “And they can also lead to significant drops in stock prices and lasting reputational damage. With identity threats becoming more severe, it’s crucial for organizations to strengthen their identity security frameworks to better protect against these growing challenges.”
IDSA executive director Jeff Reich
Furthermore, numerous security-centric compliance regulations, such as HIPAA, PCI DSS, and NIST 800-53, mandate some level of access management controls and policies, with the principle of least privilege access being a widely recommended guiding principle. By adhering to this principle, organizations can not only enhance their security posture but also ensure compliance with industry standards and regulatory requirements.
Strategies and Tactics for Implementing Least Privilege Access
While the concept of least privilege access may seem straightforward, its practical implementation across today’s complex and dynamic environments requires a strategic approach and the adoption of various tactics. By incorporating the following strategies and tactics into their identity security and access control processes, organizations can embark on a journey towards achieving least privilege access and fortifying their overall security posture.
1. Implement Appropriate Policies and Approvals for Sensitive Access
Establishing clearly defined access policies and approval protocols for sensitive roles and permissions is crucial to ensure consistent and controlled provisioning processes. Organizations should create standards for onboarding employees in different roles, making least privilege the default for all new accounts, and define procedures for managing role changes and offboarding to facilitate swift and comprehensive deprovisioning.
Educating all stakeholders, including employees, managers, and administrators, on the standardized access request and approval procedures, particularly those pertaining to sensitive, just-in-time access, is essential to ensure that policies are clear and easy to follow.
2. Transition Sensitive Access to Time-Based Access
The first step in achieving least privilege access is to identify mission-critical systems and catalog the individuals who possess privileged access to these resources, along with their associated permissions, roles, and group memberships. Subsequently, organizations should shift these Aponoments to a time-bound or contextually provisioned model, assuming by default that users do not require this level of access on a regular basis.
Granting access in these situations can be viewed as a “privileged action” escalation, where users who require elevated privileges to perform specific tasks can request just-in-time access tailored to their needs. By adopting this approach, organizations can ensure that users always have the necessary access when required, without being over-provisioned or retaining excessive privileges.
3. Automate Visibility into Sensitive Access
Achieving least privilege access hinges on gaining comprehensive visibility into who has access to what resources, permissions, and group memberships across the entire system. With the proliferation of Software as a Service (SaaS) and Infrastructure as a Service (IaaS) applications, and the centralization of management for these environments, maintaining this level of visibility can be a daunting challenge.
To address this, security teams should strive to automate the collection and centralization of access data, ensuring that information is up-to-date, easily accessible, and readily available for reference. Once the system inventory is in place, organizations should develop a schema for tagging roles, groups, and permissions within applications that are deemed most sensitive, enabling instant identification and prioritization.
4. Maintain a Comprehensive Catalog and Audit Trail
When users are granted sensitive access, it is imperative to log the decision, approvals, and the context under which the access is granted, creating an auditable trail. This information is not only useful for reviewing the necessity of access but may also serve as essential proof for external compliance requirements.
The catalog of current sensitive access should be easily accessible to IT, security, and governance, risk, and compliance (GRC) teams. Actively maintaining this catalog as part of the access review process is crucial, with users’ or identities’ statuses automatically updated in the catalog as part of the provisioning and deprovisioning processes.
5. Conduct Periodic Reviews of Sensitive Access
While defining least privilege access policies and maintaining an up-to-date catalog of active sensitive access are essential steps, it is equally crucial to regularly review sensitive access to ensure that currently provisioned access remains necessary. These reviews should not solely rely on the catalog of access or manually maintained audit trails but should also poll the applications and accounts directly to ensure that the latest and most up-to-date information is used for review. This approach ensures that any access provisioned outside of established business processes is identified, reviewed, and re-certified.
Collaborating with company managers and system administrators on periodic access reviews is a best practice for certifying that users have the appropriate levels of access. Additionally, following best practices for user access reviews can make the process more seamless and accurate.
6. Ensure Timely and Contextual Access Reviews
Access reviews are not only necessary for meeting compliance requirements but also serve as a critical tool for maintaining security by regularly identifying and removing unnecessary access. To uphold the principle of least privilege, access reviews should occur on a frequent and timely basis (at least once a quarter for privileged access) and be contextual (e.g., upon a significant role change). This level of ongoing effort necessitates automation, as manual processes may become prohibitively expensive and time-consuming.
Establishing a regular schedule for user access reviews, defining the scope of each scheduled review, and sharing this information with supporting teams can help ensure that resources are allocated appropriately and that reviews are adequately prepared for.
7. Provide Context on Access Decisions
Understanding the security implications of granted access, permissions, or group memberships is paramount when making access decisions. Downstream authorization implications of access may not always be apparent to approvers or reviewers. For instance, group memberships may have significant knock-on effects on granted permissions for resources and roles, which can be challenging to comprehend.
Regular access reviews should include context around risk, the account with access, and downstream implications of the grant. Helping those who grant and certify access understand the security implications of their decisions can empower them to make well-informed choices, ultimately strengthening the organization’s security posture.
Enhancing Access Reviews with Automation and Contextual Information
Effective access reviews are a cornerstone of maintaining least privilege access and ensuring compliance with industry regulations. However, manual processes can be time-consuming, error-prone, and ultimately ineffective in today’s complex environments. By leveraging automation and incorporating contextual information, organizations can streamline access reviews, enhance accuracy, and make more informed decisions.
Automating Access Reviews
Automating access reviews can significantly reduce the administrative burden and increase efficiency. Automated systems can collect and analyze access data from various sources, identify potential risks or policy violations, and generate reports for review. This approach not only saves time but also ensures consistency and reduces the likelihood of human error.
Automation tools can be configured to trigger access reviews based on predefined schedules or events, such as role changes, terminations, or detected anomalies. These tools can also facilitate the review process by presenting relevant information to reviewers, enabling them to make informed decisions more efficiently.
Incorporating Contextual Information
Providing reviewers with comprehensive contextual information is crucial for making informed access decisions. This information should include details about the user, their role, the resources they have access to, and the potential risks associated with that access.
Contextual information can be obtained from various sources, including user directories, asset management systems, and risk assessment tools. By integrating these data sources, organizations can present a holistic view of access rights, enabling reviewers to better understand the implications of granting or revoking access.
Additionally, incorporating risk scoring or risk ratings can help prioritize access reviews, ensuring that high-risk access privileges are reviewed more frequently or with greater scrutiny.
Striking the Balance: Least Privilege Access and Productivity
While implementing least privilege access is essential for enhancing security, it is crucial to strike a balance between security and productivity. Overly restrictive access controls can hinder employee productivity and negatively impact business operations. Conversely, lax access controls can expose the organization to significant security risks.
Enabling Self-Service Access Requests
One approach to balancing security and productivity is to implement self-service access request portals. These portals allow employees to request access to the resources they need, streamlining the process and reducing the administrative burden on IT and security teams.
Self-service portals can be integrated with automated approval workflows, ensuring that access requests are reviewed and approved based on predefined policies and risk assessments. This approach empowers employees to obtain the necessary access promptly while maintaining appropriate controls and oversight.
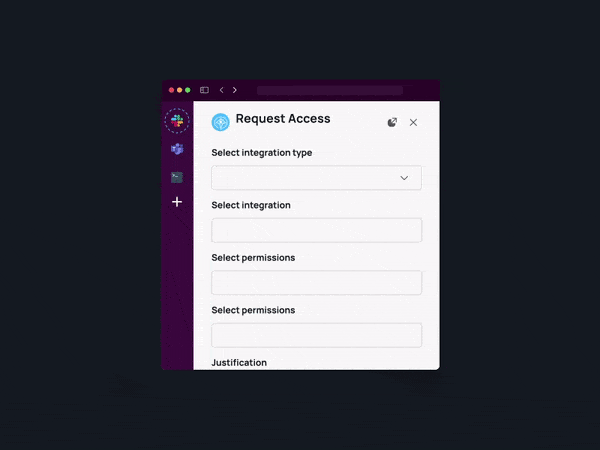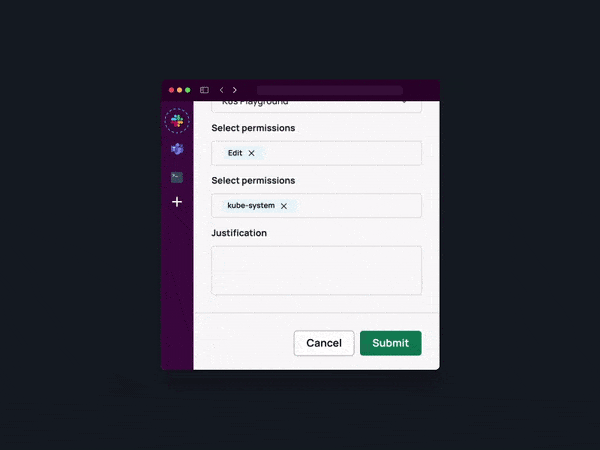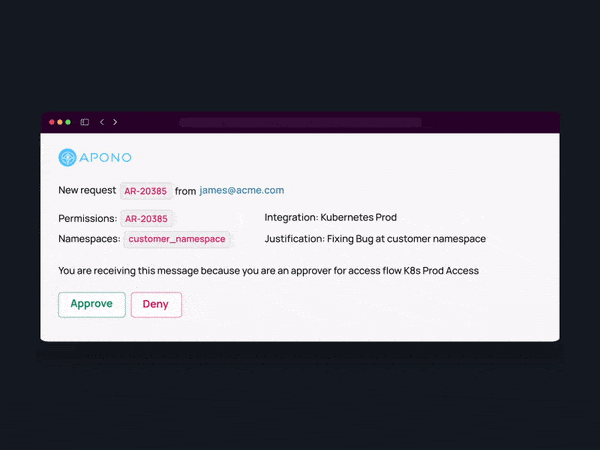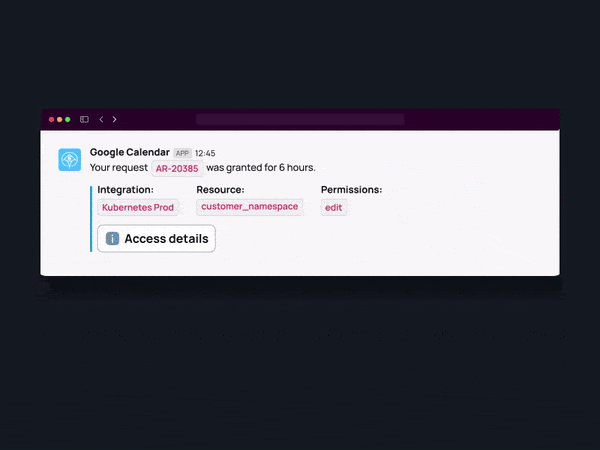
Implementing Role-Based Access Control (RBAC)
Role-Based Access Control (RBAC) is a widely adopted access management model that can help organizations achieve least privilege access while enhancing productivity. RBAC assigns access rights based on job roles or responsibilities, rather than individual users.
By defining roles and associated permissions, organizations can ensure that employees have the necessary access to perform their job functions without granting excessive privileges. RBAC simplifies access management, reduces the risk of over-provisioning, and enables efficient access provisioning and deprovisioning processes.
Educating and Training Employees
Effective implementation of least privilege access requires a strong security culture and employee awareness. Organizations should invest in educating and training employees on the principles of least privilege access, the importance of following access policies and procedures, and the potential risks associated with unauthorized or excessive access.
By fostering a security-conscious mindset among employees, organizations can encourage responsible access practices and reduce the likelihood of accidental or intentional misuse of privileges.
Continuous Monitoring and Adaptation
Achieving the balance between security and productivity is an ongoing process that requires continuous monitoring and adaptation. Organizations should regularly review their access management policies, procedures, and technologies to ensure they remain effective and aligned with business needs.
Monitoring user behavior, access patterns, and security incidents can provide valuable insights into areas that may require adjustments or additional controls. By continuously adapting and refining their access management strategies, organizations can maintain an optimal balance between security and productivity.
Addressing Challenges in Implementing Least Privilege Access
While the benefits of implementing least privilege access are clear, organizations often face various challenges in their pursuit of this principle. Addressing these challenges proactively can ensure a smoother implementation process and increase the likelihood of success.
Overcoming Legacy Systems and Technical Limitations
Many organizations rely on legacy systems or applications that were not designed with modern access management principles in mind. These systems may lack robust access control mechanisms, making it difficult to implement least privilege access effectively.
To overcome this challenge, organizations may need to explore integration solutions or third-party access management tools that can bridge the gap between legacy systems and modern access control practices. Additionally, organizations should consider migrating to more modern and secure platforms as part of their long-term strategy.
Managing Access in Hybrid and Multi-Cloud Environments
With the increasing adoption of cloud computing and the prevalence of hybrid and multi-cloud environments, managing access across different platforms and providers can be a significant challenge. Each cloud provider may have its own access management tools and policies, making it difficult to maintain a consistent and centralized approach to least privilege access.
To address this challenge, organizations should consider implementing a centralized identity and access management (IAM) solution that can integrate with multiple cloud providers and on-premises systems. This approach enables consistent access policies, centralized visibility, and streamlined access management across the entire IT environment.
Ensuring Compliance with Regulations and Standards
Compliance with industry regulations and standards, such as HIPAA, PCI DSS, and NIST 800-53, often mandates the implementation of least privilege access principles. However, demonstrating compliance can be a complex and time-consuming process, especially in large organizations with diverse IT environments.
To simplify compliance efforts, organizations should leverage automated tools and processes for access management, access reviews, and audit trail maintenance. Additionally, implementing a comprehensive governance, risk, and compliance (GRC) framework can help organizations streamline compliance activities and ensure that access management practices align with regulatory requirements.
Fostering Collaboration and Buy-In Across Teams
Implementing least privilege access often requires collaboration and buy-in from various teams within an organization, including IT, security, compliance, and business units. Lack of alignment or resistance to change can hinder the successful implementation of least privilege access strategies.
To foster collaboration and buy-in, organizations should establish clear communication channels, involve stakeholders from different teams in the planning and implementation process, and provide training and education to ensure a shared understanding of the benefits and importance of least privilege access.
Maintaining Visibility and Control in Dynamic Environments
In today’s dynamic IT environments, where users, applications, and resources are constantly changing, maintaining visibility and control over access rights can be a significant challenge. Manual processes for access management and reviews may quickly become outdated or ineffective.
To address this challenge, organizations should implement automated access management solutions that can continuously monitor and update access rights based on changes in the environment. Additionally, leveraging artificial intelligence and machine learning technologies can help organizations identify potential access risks and anomalies in real-time, enabling prompt remediation.
The Future of Least Privilege Access: Emerging Trends and Technologies
As technology continues to evolve, the implementation of least privilege access principles will also need to adapt to new challenges and opportunities. Staying informed about emerging trends and technologies can help organizations stay ahead of the curve and maintain a robust security posture.
Zero Trust Network Access (ZTNA)
Zero Trust Network Access (ZTNA) is an emerging security model that aligns closely with the principles of least privilege access. ZTNA assumes that no user or device should be trusted by default, regardless of their location or network connection.
By implementing ZTNA, organizations can enforce least privilege access at the network level, granting access to specific applications or resources based on predefined policies and user context. This approach can significantly reduce the attack surface and mitigate the risks associated with unauthorized access or network-based threats.
Privileged Access Management (PAM) Solutions
Privileged Access Management (PAM) solutions are designed to secure and control access to privileged accounts and sensitive resources. These solutions often incorporate least privilege access principles by providing granular access controls, session monitoring, and auditing capabilities.
By implementing PAM solutions, organizations can ensure that privileged access is granted only when necessary, with appropriate approvals and logging mechanisms in place. This approach can help mitigate the risks associated with privileged account misuse or compromise, further enhancing the organization’s security posture.
Continuous Adaptive Risk and Trust Assessment (CARTA)
Continuous Adaptive Risk and Trust Assessment (CARTA) is an emerging concept that combines risk assessment, trust evaluation, and adaptive access controls. CARTA continuously monitors user behavior, device posture, and environmental factors to dynamically adjust access privileges based on perceived risk levels.
By implementing CARTA, organizations can achieve a more granular and context-aware approach to least privilege access. Access rights can be automatically adjusted based on real-time risk assessments, ensuring that users only have the necessary privileges for their current context and minimizing the potential for unauthorized access or misuse.
Blockchain-Based Access Management
Blockchain technology, known for its decentralized and immutable nature, is being explored as a potential solution for secure access management. By leveraging blockchain, organizations can create a tamper-proof audit trail of access events, ensuring transparency and accountability.
Additionally, blockchain-based access management solutions can enable decentralized access control, where access policies and decisions are distributed across multiple nodes, reducing the risk of a single point of failure or compromise.
While still an emerging concept, blockchain-based access management holds promise for enhancing the implementation of least privilege access principles, particularly in environments where trust and transparency are critical.
Conclusion
Implementing the principle of least privilege access is a critical endeavor for organizations seeking to fortify their security posture, mitigate risks associated with account compromises and insider threats, and ensure compliance with industry regulations. By adopting the strategies and tactics outlined in this comprehensive guide, organizations can navigate the complexities of modern identity environments and achieve a robust least privilege access implementation.
However, it is essential to recognize that least privilege access is not a one-time effort but rather an ongoing process that requires continuous monitoring, adaptation, and alignment with emerging trends and technologies. By staying informed and embracing innovation, organizations can future-proof their least privilege access strategies and maintain a resilient security posture in the face of evolving threats and challenges. Embracing a mindset of continuous improvement and staying abreast of industry best practices will enable organizations to refine and enhance their least privilege access implementation over time, ensuring optimal security while maintaining operational efficiency.
How Apono Helps
Apono plays a pivotal role in reinforcing the Principle of Least Privilege by providing robust access management solutions that ensure users have only the minimum levels of access necessary for their roles. This approach significantly reduces the risk of unauthorized access and potential security breaches. Apono’s advanced features, including granular permission settings and real-time monitoring, allow organizations to meticulously control and review access rights. By automating the provisioning and de-provisioning processes, Apono ensures that permissions are promptly adjusted as employees’ roles change, thereby preventing privilege creep. Furthermore, its comprehensive auditing capabilities facilitate regular reviews and compliance checks, ensuring adherence to regulatory requirements and internal policies. Overall, Apono’s integration into an organization’s security framework enhances operational efficiency while upholding strict access control measures consistent with the Principle of Least Privilege.





