10 Must-Have Elements for an Air-Tight IT Security Policy
In 2023, data security faced an uphill battle against cyberattacks, and the risks of becoming a victim grew stronger.
There was a shocking 600% surge in cybercrime, with the average breach costing $4.37 million to recover from. The figures are up across the board, with cyberattacks occurring globally every 14 seconds.
Despite these unnerving statistics, there is a silver lining. There are many ways to stay ahead of attacks and create a robust defense against cyber threats, including creating an IT security policy.
What is an IT Security Policy?
An IT security policy provides guidelines for utilizing and securing your organization’s IT assets. The goal is to ensure you take all the necessary steps to protect against cyber threats, build a culture of security awareness, and outline acceptable cybersecurity behaviors.
Security policies are not one-size-fits-all. Each organization has unique requirements and risks, and a well-defined IT security policy should consider your organization’s specific needs and industry best practices.
IT Security Policy vs Data Security Policy: Key Differences
Although both IT security and data protection aim to safeguard data, they function at different levels and serve distinct purposes. IT security encompasses a holistic approach to protecting all forms of information assets, while data protection specifically targets personal or sensitive data:
- IT Security Policy: Acts as the castle walls, protecting everything within from unauthorized access.
- Data Security Policy: Focuses on safeguarding the valuables (data) stored within the castle walls.
Organizations must prioritize information security and data protection to establish a strong and compliant data protection framework. This synergy ensures the confidentiality, integrity, and availability of data while respecting individuals’ rights and privacy.
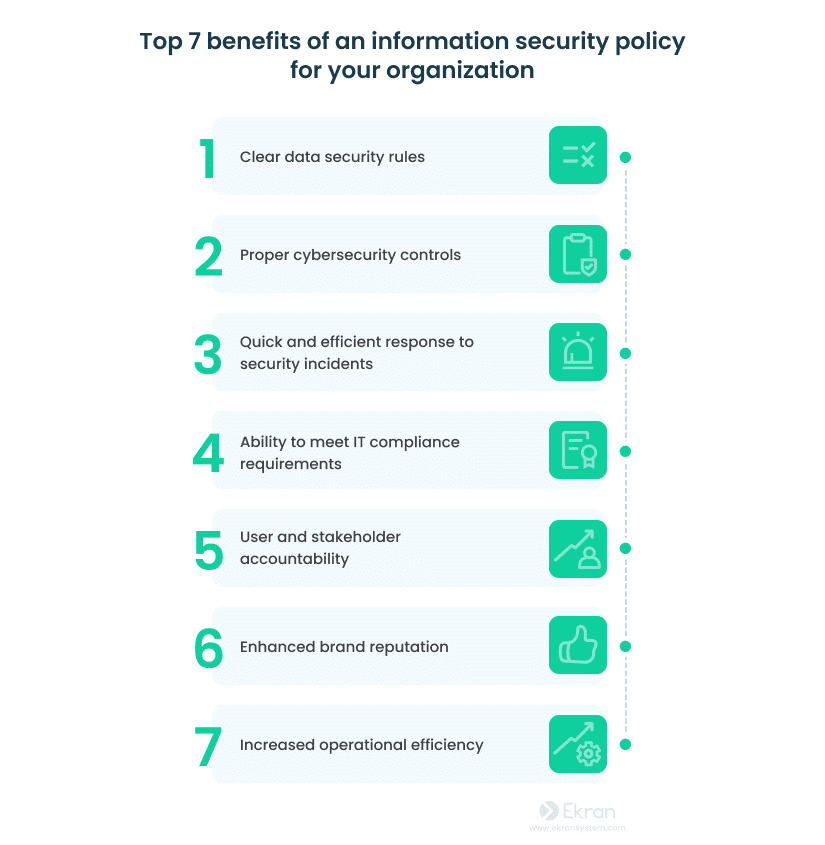
Why an IT Security Policy is Important
There are many reasons why an IT security policy is a must-have for your business.
- Attack protection and risk reduction: Without a comprehensive IT security policy in place, your organization is vulnerable to cyberattacks, data breaches, and legal implications – not to mention the loss of customer trust.
- Build a culture of security: By establishing a policy, you can ensure that all stakeholders and employees understand their roles and responsibilities in safeguarding sensitive information.
- Close all gaps: You can identify vulnerabilities and build your policy accordingly.
- Meet regulatory requirements: Compliance requirements are complex and constantly changing, and your policy can help you stay on top of regulatory expectations.
10 Essential Elements of an IT Security Policy
An effective IT security policy should encompass several vital elements that work together to build your organization’s cyber resilience.
- Establishing Security Objectives and Goals
The first step in creating an IT security policy is defining your organization’s security objectives and goals, which should align with your overall business objectives and consider your risk appetite. As you define your goals, you should evaluate how to achieve these three key objectives for IT security:
- Confidentiality: Defining which individuals can access data and assets.
- Integrity: Keeping data accurate, complete, and operational.
- Availability: Ensuring data is always available for users.
By taking the time to establish security objectives and goals, you create a strong foundation for your IT security policy. This foundation ensures your policy is tailored to your organization’s specific needs and helps you build a robust security posture to protect your valuable information assets.
- Roles and Responsibilities in IT Security
Defining roles and responsibilities is crucial for ensuring accountability among employees and identifying to whom the IT security policy applies. An effective policy should clearly outline the responsibilities of each stakeholder involved in IT security, including employees, managers, and IT personnel.
Clearly defined roles and responsibilities ensure everyone understands:
- Who is accountable for IT security: This eliminates confusion and finger-pointing in case of a security incident.
- What is expected of them: Employees know what they need to do to contribute to a secure environment.
- Who to contact for help: Users know who to report suspicious activity or seek assistance with security concerns.
Key players include:
- Senior Management
- IT Department
- End Users
- Security Awareness Trainer
- Data Privacy Officer (DPO)
- Risk Management Team
- Risk Assessment and Management
A robust risk assessment and management framework involves:
- Identifying potential threats and unknown vulnerabilities.
- Evaluating the likelihood and impact of each threat.
- Implementing appropriate controls to mitigate the risks.
Your IT security policy should mandate regular risk assessments to identify emerging cyber threats and make necessary and ongoing adjustments. The policy should also outline how identified risks will be addressed, which could involve implementing security controls, patching vulnerabilities, or conducting security awareness training for employees.
- Incident Response and Reporting Procedures
Even with the best security measures in place, incidents can still occur. An effective IT security policy includes clear procedures for reporting and responding to security incidents. For example:
- Establishing a dedicated incident response team.
- Defining communication channels.
- Delegating responsibility.
- Outlining the steps to take in case of a breach or incident.
Prompt and effective incident response can minimize the impact of a security breach and help you recover quickly. This preparedness helps mitigate damage, minimize disruption, and get your organization back on track. Remember, a successful incident response relies on a combination of planning, clear communication, and a skilled incident response team.
- Regular Security Audits and Assessments
Regular security audits and assessments help you keep up with ongoing compliance and monitor the effectiveness of the IT security policy. Audits help identify any gaps or weaknesses in the security measures and provide an opportunity to make necessary improvements to stay proactive in addressing potential vulnerabilities and enhancing your overall security posture.
- Classify Your Data
Data classification is a method of categorizing data based on who is responsible for it, its risk level, and access control requirements (such as removing standing privileges). For example, you could categorize data into these levels:
- Publicly available data that poses a low cybersecurity risk.
- Sensitive data that would not harm your organization if leaked.
- Sensitive data that could cause harm to your organization if leaked.
- Sensitive data that would definitely cause harm and put you in the firing line if leaked.
- Build a Culture of Security Awareness
An IT security policy is only helpful if it is properly enforced. Therefore, it’s up to your employees to do their part and withhold the policy. Due to this expectation, you may need to implement training sessions covering topics like social engineering attacks and data protection best practices to minimize the risk of human error.
- Keep an Eye on Compliance
The regulatory landscape is a complex minefield. Your organization must understand industry-specific compliance requirements like SaaS and HIPAA and ensure the IT security policy covers everything required to meet standards like PCI DSS and GDPR.
- Engage Stakeholders
Executing your IT security policy uniformly and successfully is impossible without a commitment from the C-suite. Senior managers are busy, and it’s your responsibility to secure their buy-in and explain why and how the policy is relevant.
- Continuous Improvement
Remember, an effective IT security policy is not a one-time effort. Continuous evaluation and improvement are required to keep up with the changing threat and regulatory landscape. You can maintain a secure digital environment and protect your assets by staying proactive and adapting to new challenges.
Implementing an IT security policy is an investment in your long-term success and reputation, and organizations that prioritize security will not only protect their data but also gain the trust and confidence of their customers and stakeholders.
Don’t Forget to Define Access with Apono
By including the essential elements of an air-tight IT security policy, your organization can mitigate the risk of cybersecurity breaches and protect valuable assets from falling into the wrong hands.
The final essential element of an excellent IT security policy is controlling access. Apono’s cloud-native access management solution serves as an integral part of your policy, helping you significantly limit your attack surface by removing standing privileges that could leave your organization vulnerable to identity-based attacks.
Apono enables automated dynamic permissions based on organizational context and approval workflows, right down to the database level, so you can prevent human error and streamline compliance requirements.
Get started with Apono for free.