8 Privileged Access Management (PAM) Best Practices for Cloud Infrastructure

Rom Carmel
January 6, 2025
Even the simplest mistakes can leave your data wide open to cyber threats. If the worst happens and there’s an attack, cybercriminals gain free-for-all access to your cloud resources.
They tamper with your data, disrupt workflows, and steal sensitive information, meaning the need for Privileged Access Management (PAM) best practices are more indispensable than ever for any robust cloud security strategy. According to a recent study, the global PAM market is expected to grow from $2.9 billion in 2023 to $7.7 billion by 2028, cementing its position in the cybersecurity landscape.
Privileged Access Management in a Nutshell
Privileged Access Management (PAM) centers on securing privileged accounts with elevated permissions. It is a cybersecurity strategy that controls and monitors access to critical systems and sensitive information from unauthorized access. Without it, privileged accounts can become the primary targets for cybercriminals, putting the entire organization at risk.
Here’s how PAM works in a nutshell:
- It identifies all privileged accounts across the network.
- After identification, credentials like passwords and keys are securely stored in an encrypted vault.
- The principle of least privilege is applied to restrict access based on user roles and necessity.
- Finally, you can use auditing to track who accessed what, when, and why to detect anomalies and generate reports to help maintain security and compliance.
Types of Privileged Accounts
- Service Accounts
Applications, automated processes, and IT systems commonly use service accounts. Consider the devastating SolarWinds hack in 2020, where attackers found vulnerabilities in the service accounts and gained access to critical data and systems.
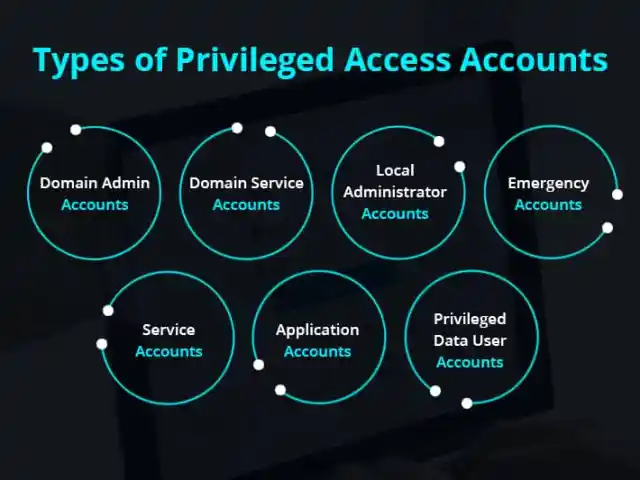
- Domain Administrator Accounts
Domain administrator accounts have full control over an organization’s IT infrastructure, making them attractive targets for attackers. An example is the Microsoft Exchange Server attacks in early 2021, where hackers gained control through privileged accounts, escalating their access across domains.
- Emergency Accounts or “Break-Glass” Accounts
Break-glass accounts are special accounts that can bypass authentication, monitoring processes, and standard security protocols. If not properly managed, they present significant risks.
3 Key Challenges of Implementing Privileged Access Management Best Practices
- Forgotten and Overextended Privileges
In implementing Privileged Access Management (PAM) best practices, you must ensure that access to critical resources is both temporary and purposeful. Often, privileges are left open long after a task is completed, such as contract or consulting engineers retaining production permissions and indefinite access to sensitive data lakes.
- Lack of Efficient Access Management
As your business grows, so does the complexity of managing privileges, especially in environments with many resources and frequently changing requirements. A solution that works for an organization of ten might crumble under an organization of 1,000. In this case, managing permissions for each cloud resource every time access is required becomes inefficient.
- Ensuring Data Privacy While Managing Access
Another PAM implementation challenge is managing access to sensitive data while ensuring privacy. Many solutions require storing or caching sensitive credentials, posing a data security risk.
8 Privileged Access Management Best Practices for Cloud Infrastructure
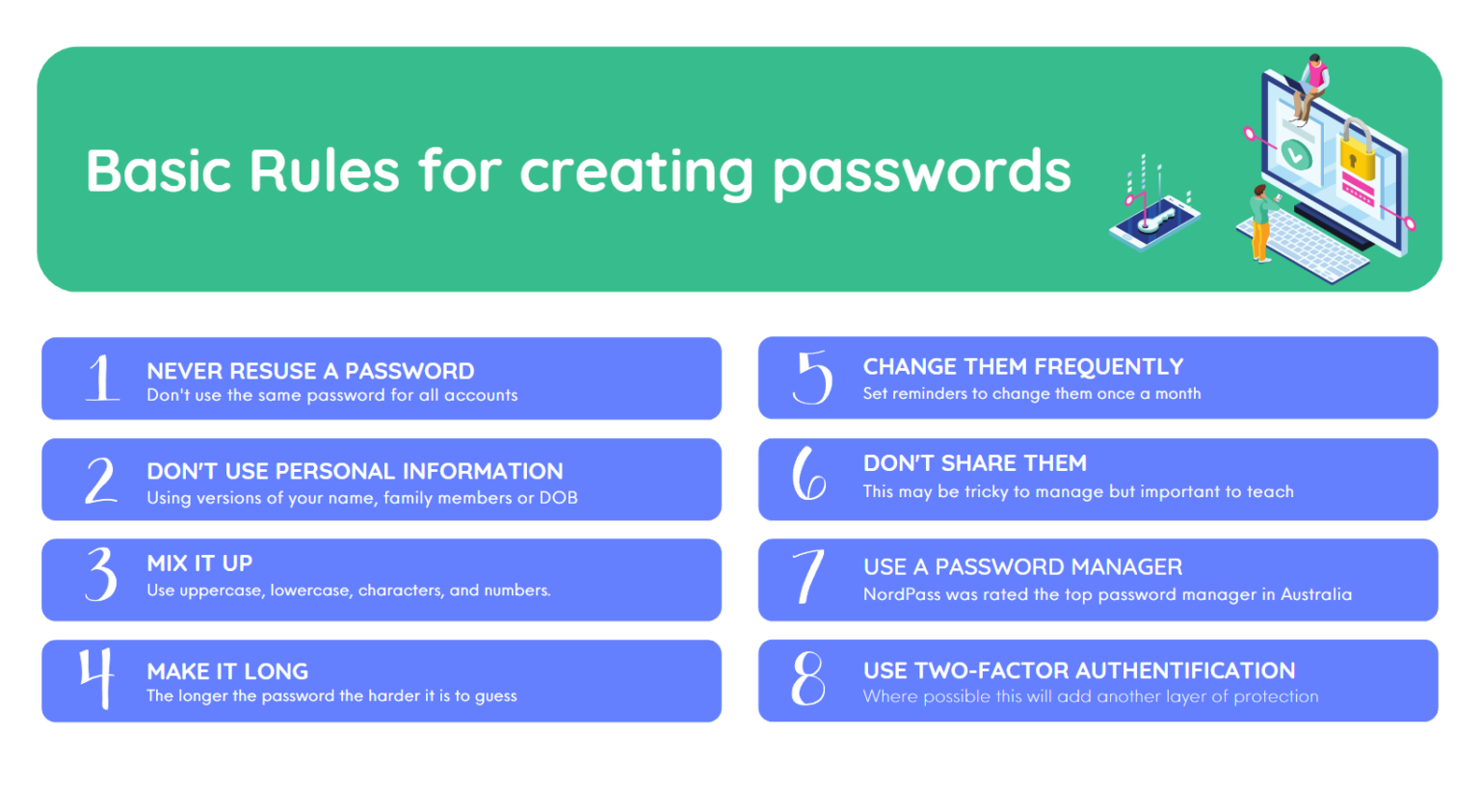
- Use Strong Password Policies
Implementing strong password policies can help reduce the chances of credential theft. Use complex, unique passwords and enforce regular password rotations. Employees should already know to steer clear of the classic phone numbers or dates of birth!
- Implement the Principle of Least Privilege (PoLP)
PoLP is and has always been the first principle of the cloud. The principle of least privilege states that users should only have the minimum level of access necessary to perform their tasks. In other words, a user who does not need admin rights should not have them.
- Use Identity and Access Management (IAM) and Role-based Access Control (RBAC) Policies
IAM allows organizations to define who can access resources under what conditions. Role-Based Access Control (RBAC), on the other hand, helps manage who has access to cloud resources by defining roles and associating them with the required permissions.
For example, in AWS, you can create custom IAM roles for developers, admins, and security personnel, each with tailored permissions. Use managed policies and avoid using root accounts for daily operations.
- Multi-factor Authentication (MFA)
Another best practice is to use multiple forms of verification (e.g., a mix of your password and biometric scan, a time-based code from your device, or a hardware token) before gaining access to privileged accounts. MFA adds an extra layer of security, reducing the risk of compromised credentials by requiring something the attacker doesn’t have. So, even when attackers get hold of your credentials, they still won’t be able to gain access to your account.
Integrate MFA into your Privileged Access Management (PAM) solution for all privileged accounts and enforce it for high-risk accounts like administrators or service accounts. You can use cloud-specific solutions like AWS MFA, Azure Multi-Factor Authentication, or Google Cloud’s Identity Platform.
5. Automate Access Management and Provisioning
Over 68% of security breaches are caused by human errors. Manually managing access can cause these errors, particularly as your organization scales. Use automation tools like Apono to ensure that permissions are granted and revoked in a timely, accurate, and consistent manner.
6. Secure Privileged Access with Encryption
Encrypting privileged access is essential for maintaining confidentiality, especially for access to sensitive data and resources. This best practice ensures the data remains secure even if an attacker gains unauthorized access to privileged credentials.
Encryption protocols like AES-256 protect sensitive data in transit and at rest. Another tip is to ensure that cloud credentials, secrets, and other sensitive data are stored securely in encrypted vaults such as AWS Secrets Manager, Azure Key Vault, or Google Cloud Secret Manager.
- Segmenting Critical Systems
Segmenting critical systems limits access to sensitive data. It reduces the risk of lateral movement in case of a breach, involving isolating high-risk systems and implementing access control for every segment of your workload. This way, your organization can ensure that unauthorized users cannot easily traverse the entire network, making it even harder for attackers to compromise multiple systems at once.
- Educate and Train Privileged Users
Privileged users should be trained on security best practices, as they play a vital role in managing sensitive systems and resources. The training could focus on the latest external and insider threats, including phishing, malware, and social engineering tactics, with real-world examples of how mishandled privileges can lead to breaches. Rewarding users who identify vulnerabilities or report suspicious activity can encourage proactive behavior.
Cloud environments often require privileged users to access programmatic APIs, which requires secure handling. In this example, training should highlight best practices for securing API keys using tools like AWS Secrets Manager or Azure Key Vault.
For developers, additional emphasis should be placed on avoiding hardcoding credentials into code or scripts, as these can easily be leaked or exploited. Take a look at this Python script, which exposed the AWS access and secret keys:
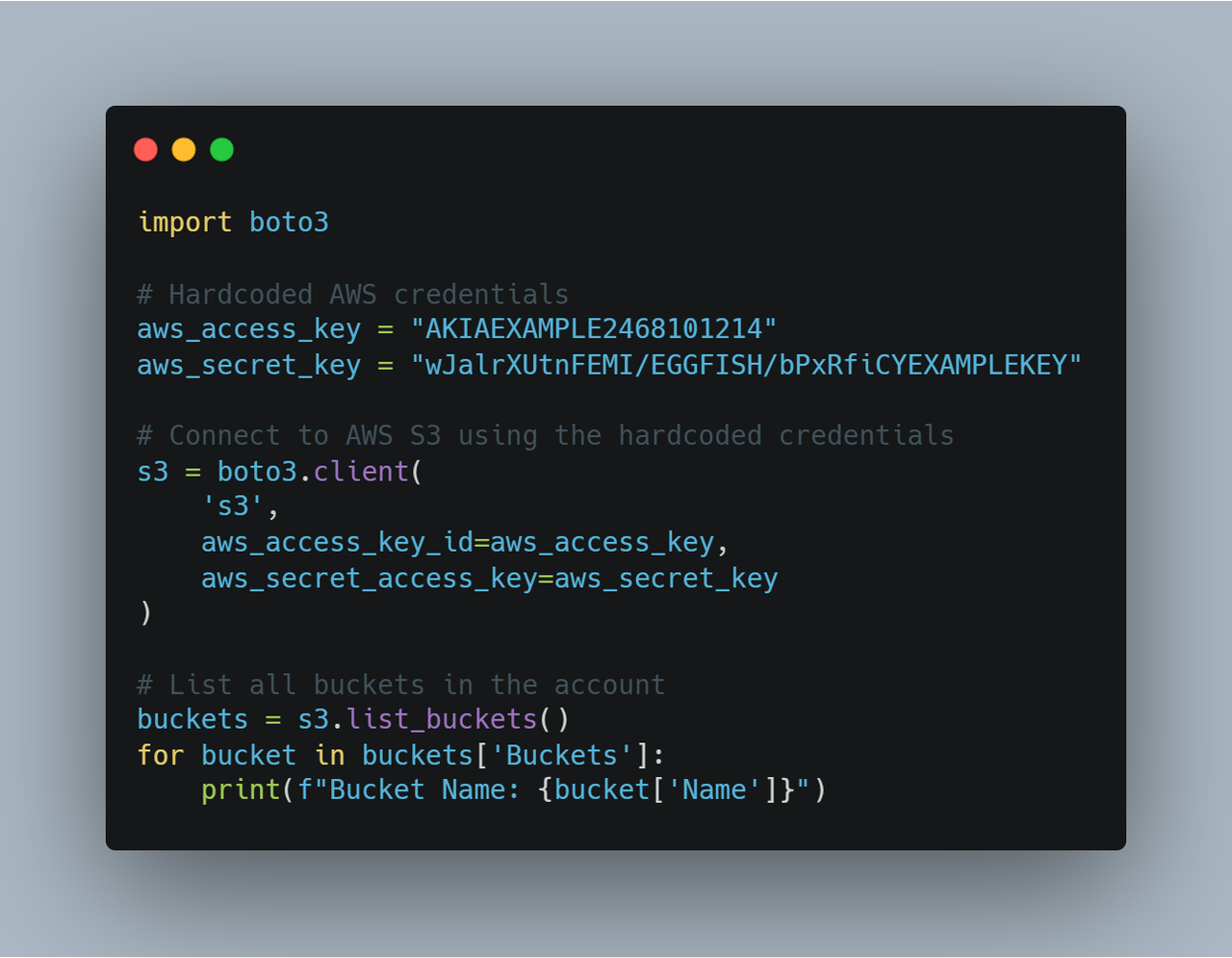
If the above code is shared, pushed to a public repository (e.g., GitHub), or leaked, anyone with access to it can misuse your AWS credentials. Alternatively, you can use a secrets management tool like AWS Secrets Manager to securely store and access credentials:
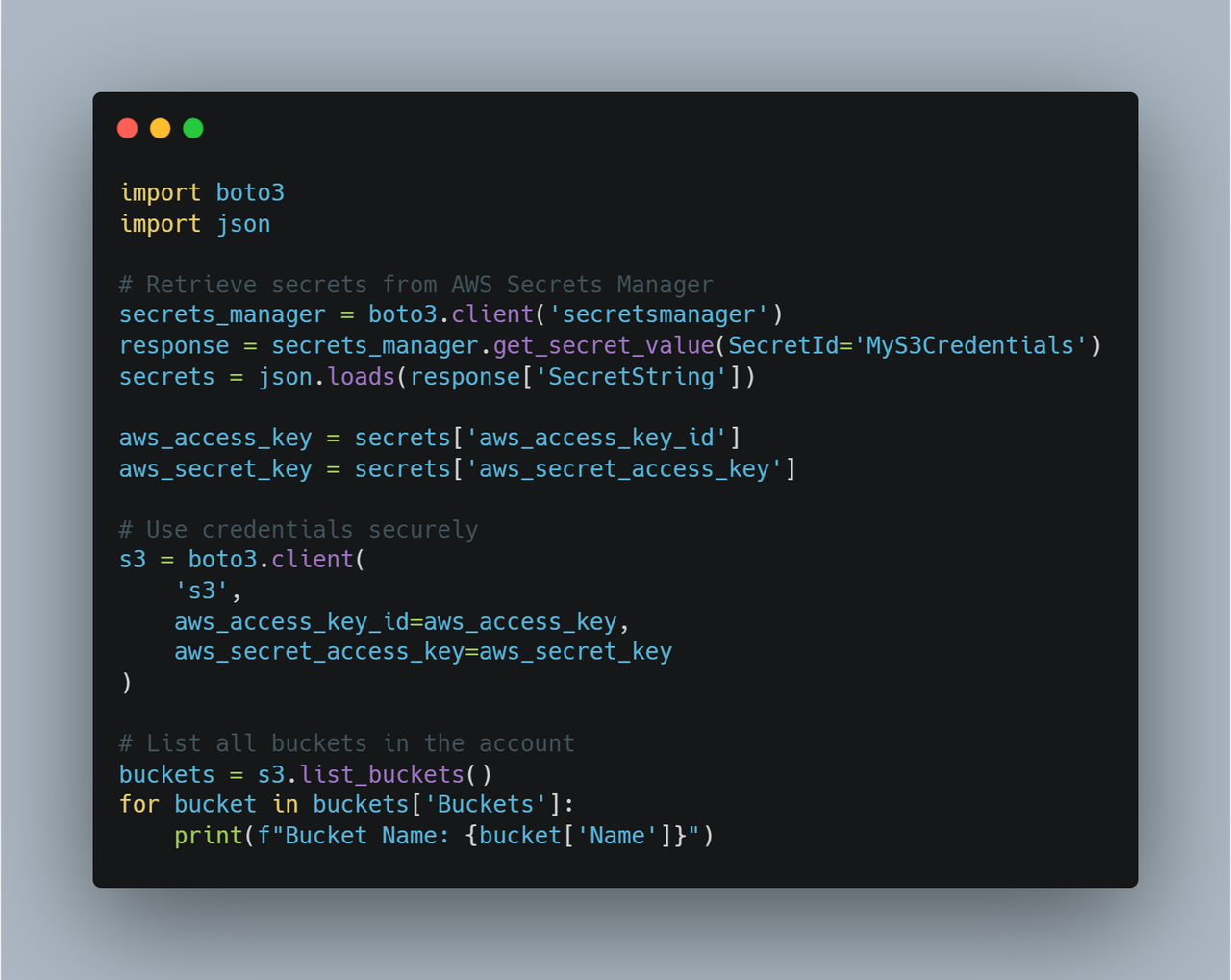
Finally, effective training is not a one-time event but an ongoing process. Cloud security is an ever-evolving field; privileged users must stay updated on emerging threats and best practices. Providing documentation, maintaining an up-to-date knowledge base, and delivering periodic refresher training ensures that users remain informed and vigilant.
Reduce Access Risks by 95% With Apono
Failing to implement Privileged Access Management (PAM) best practices is like leaving the keys to your castle lying out in the open. As we’ve explored, PAM is crucial for controlling and monitoring access to your most critical assets, preventing devastating breaches that can disrupt operations, compromise sensitive data, and damage your reputation.
With Apono, you can reduce your access risk by a huge 95% by removing standing access and preventing lateral movement in your cloud environment. Apono enforces fast, self-serviced, just-in-time cloud access that’s right-sized with just-enough permissions using AI.
Discover who has access to what with context, enforce access guardrails at scale, and improve your environment access controls with Apono. Book a demo today to see Apono in action.





