Access Threat Detection & Response
Cloud-Native Access Governance
Cloud-Native Access Governance
Cloud environments are often distributed across multiple regions and providers, with resources and services being spun up or down dynamically. This complexity makes it difficult to maintain visibility and consistent identity threat detection across the entire environment. Allowing threats to go unnoticed until significant damage has been done.
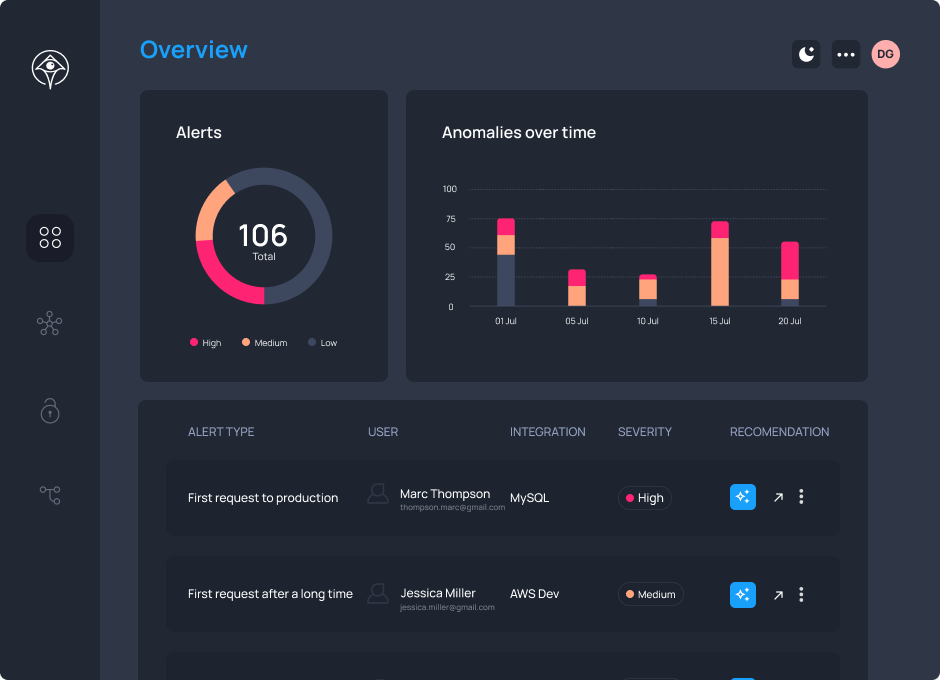
Stop attackers before they impact your sensitive resources with continuous monitoring for anomalous access request activity.
Stop attackers before they impact your sensitive resources with continuous monitoring for anomalous access request activity.
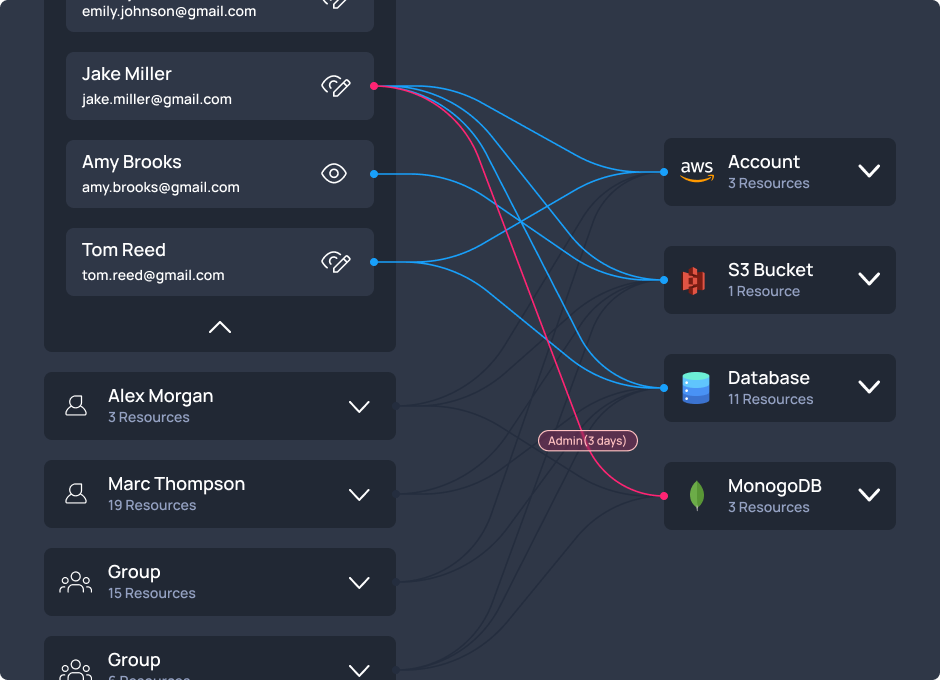
Mitigate threats more efficiently by leveraging continuous, detailed auditing of access and actions, enabling your team to get the full picture and respond effectively faster.
Mitigate threats more efficiently by leveraging continuous, detailed auditing of access and actions, enabling your team to get the full picture and respond effectively faster.
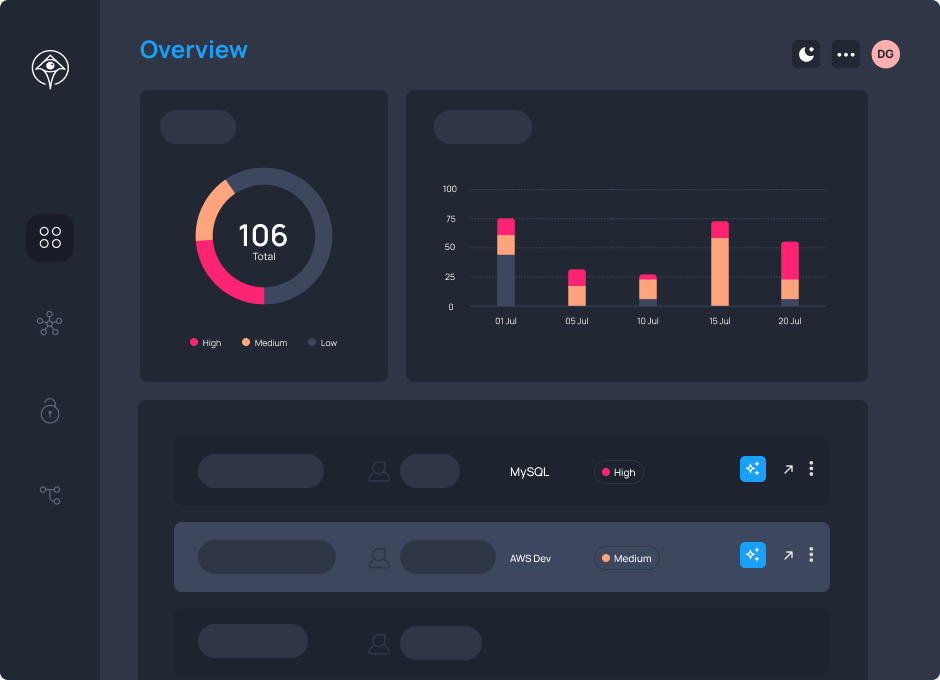
Stop attacks instantaneously when anomalous activity is detected, blocking access directly to the source with a single click.
Stop attacks instantaneously when anomalous activity is detected, blocking access directly to the source with a single click.
“
“We’ve reduced the amount of time it takes people to get access to the things they need to do their job. We freed up the team’s time. And on top of that, we’re preventing tens of millions of dollars of potential data breach”.
Director of Cloud Infrastructure