Attack Surface
An attack surface in permissions management refers to the sum total of all potential vulnerabilities that an unauthorized entity could exploit to gain access to a system or data. ...
Role-Based Access Control (RBAC) is a method for managing and controlling access to computer systems and data within an organization. It is a widely used access control model that is designed to improve security and simplify the management of permissions and user access.
In Role-Based Access Control, access permissions are tied to roles, and users are assigned to one or more roles based on their job responsibilities or functions within the organization. Here’s how it works:
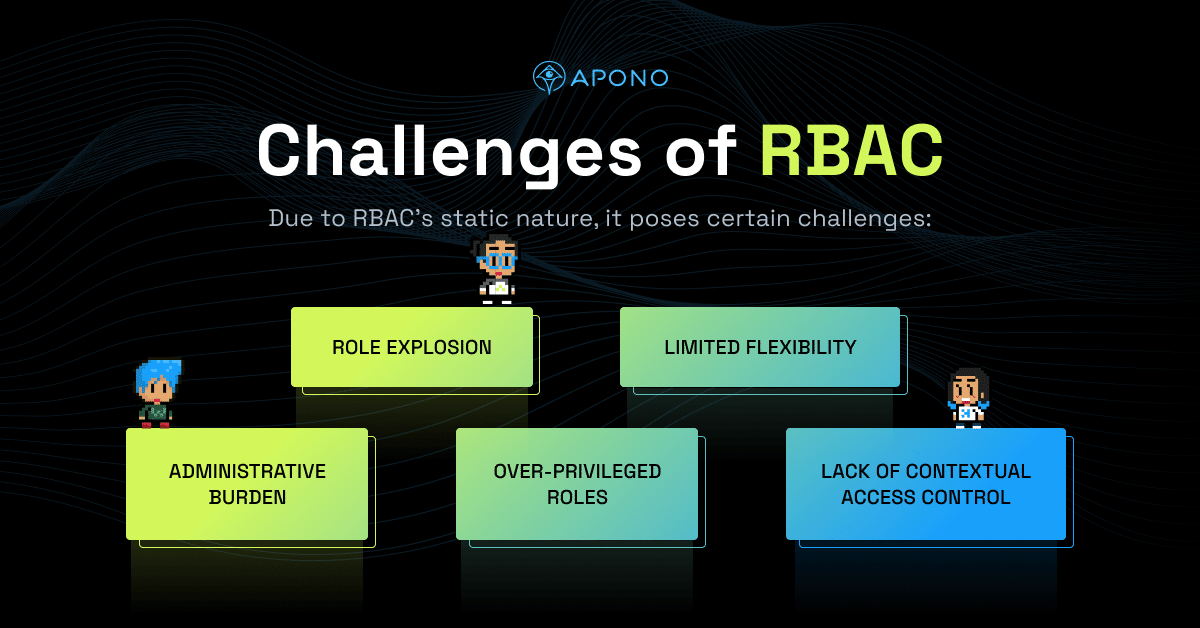
While Role-Based Access Control (RBAC) offers several advantages, it does come with certain challenges, particularly its static nature. The static nature of RBAC refers to the fact that role assignments and permissions are typically defined and assigned in advance, without considering dynamic factors or changing access requirements. This static approach can pose challenges in certain scenarios:
To address these challenges, organizations can consider incorporating more dynamic access control mechanisms alongside Role-Based Access Control. This could include implementing Just-In-Time (JIT) access, Attribute-Based Access Control (ABAC), or dynamic role assignment based on specific user attributes or conditions. These approaches provide more flexibility and adaptability in managing access while complementing the structure and benefits of RBAC.
By combining RBAC with dynamic access control mechanisms, organizations can strike a balance between providing necessary access and maintaining security, enabling a more agile and context-aware approach to access management.
About Apono
Apono is a leading provider of access management solutions that helps address the limitations of RBAC (Role-Based Access Control) and enhances access control with dynamic mechanisms. With Apono’s platform, organizations can leverage Just-In-Time (JIT) access and Attribute-Based Access Control (ABAC) functionalities to achieve a more flexible and adaptable access management approach.
Apono’s JIT access capability allows organizations to grant temporary access to specific resources based on immediate needs, overcoming the static nature of RBAC. By incorporating JIT access, organizations can improve security by reducing the attack surface and minimizing the risk of unauthorized access.
In addition, Apono integrates ABAC, enabling organizations to define access control policies based on attributes such as user attributes, context, or specific conditions. This granular and contextual access control enhances flexibility by considering factors like time, location, and data sensitivity. Apono’s ABAC functionality provides organizations with the flexibility to manage access permissions based on dynamic attributes and changing requirements.
By combining Role-Based Access Control with Apono’s dynamic access mechanisms, organizations can achieve a comprehensive and adaptable access management solution. Apono’s platform empowers organizations to provide timely and context-aware access to resources while ensuring security and compliance. Experience the benefits of Apono’s enhanced access control and improve your organization’s access management strategy.
A
B
C
D
F
G
H
I
J
L
M
O
P
R
S
T
V
Z